BYOD Policies for Organizations (4 Examples)

Using our own devices for both personal and business purposes can bring greater flexibility, efficiency, and mobility to our daily routines. At the same time, bring-your-own-device (BYOD) programs introduce security, privacy, and usage concerns. Customized BYOD policies for organizations are an effective way to mitigate potential risks.
What is a BYOD policy?
A bring our own device (BYOD) policy is a written set of ground rules that describes how, when, and where employees can use personal devices to conduct company business. 75% of employees are already using their own cell phones for work, and 83% of companies have a BYOD policy in place. As these practices grow in popularity, BYOD policies for organizations can help maximize the benefits while minimizing security risks.
Want to learn more about using Dashlane Password Manager at home or at work?
Check out our personal password manager plans or get started with a free business trial.
4 examples of BYOD policies
Before you update or implement a BYOD company policy, it’s important to review some of the various program types. These BYOD policy examples reflect the many ways organizations can implement policies that best suit their preferences and culture.
- Full BYOD: This category allows employees to select their own device type or use a device they already own. A full BYOD policy covers employees who only use their own devices for work and aren’t provided with a company-owned device. Full BYOD can blur lines for acceptable use and offboarding practices since direct company control is limited.
- Hybrid BYOD: With hybrid policies, employees have the flexibility to use both their own device and an employee-owned device like a desktop or laptop computer. The company might choose to add guidelines that restrict the use of personal devices to things like email and messaging apps that don’t directly involve sensitive company data.
- Work from home BYOD: The rise in working from home (WFH) has increased the chances of employees using their own devices, personal space, and internet connections for company business. Remote working has made the modern workplace much more flexible but adds additional cybersecurity concerns when factors like unsecured WiFi and lax rule enforcement are coupled with BYOD. A work-from-home BYOD policy should address these important issues.
- Corporate-owned, personally enabled (COPE): This BYOD model allows businesses to leverage economies of scale for better pricing on devices and data plans. Employers then provide the devices directly to employees for a combination of personal and business use. This type of arrangement removes any ambiguity regarding device ownership, app restrictions, and requirements for password manager apps and other company-directed security features. Employees are usually free to use their COPE devices for personal use during their off hours.
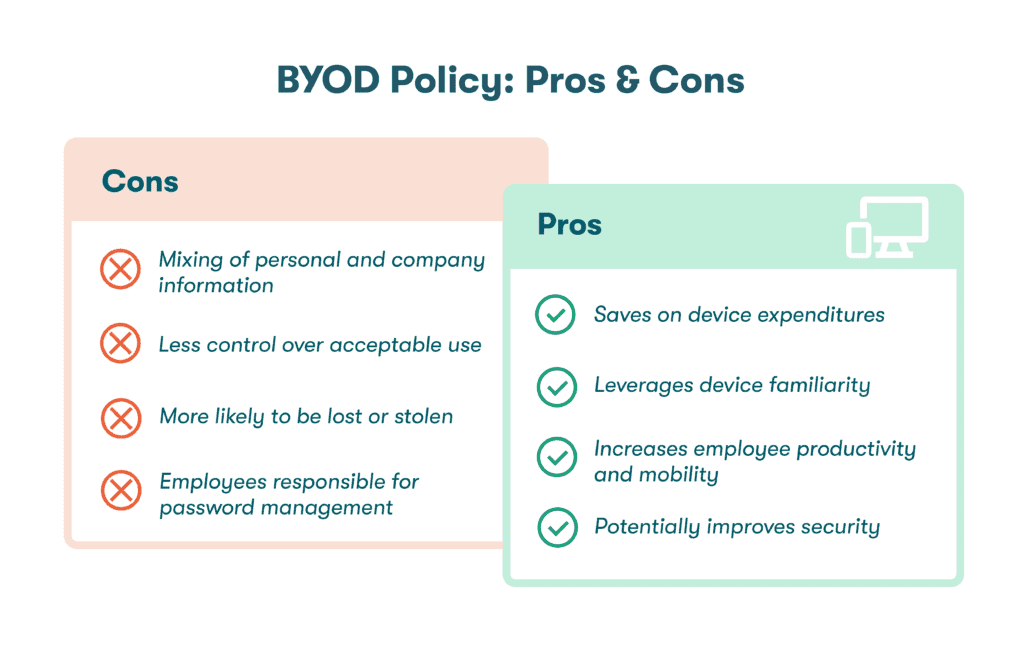
The benefits of implementing a BYOD program
With the right policy in place, a BYOD program can benefit both employers and employees. An effective, well-designed BYOD program has the following benefits:
- Saves money on device expenditures: Most workers in the U.S. already own laptops, cell phones, and other types of devices. When employees are willing to use their personal devices for work purposes, this can save companies a lot of overhead costs. Many businesses purchase new laptops and cell phones for every new employee to avoid device wiping and refurbishment. Eliminating these repeat purchases can produce huge savings over time.
- Leverages device familiarity: When employees are familiar with the device’s functions and features, the learning curve for new apps is less steep, and navigation is more efficient. If workers are allowed to choose their preferred device type as part of a flexible BYOD policy, they’re likely to replace an arbitrary company choice with something they’re familiar with and comfortable using.
- Makes employees more productive: Studies have shown that employees who use their own devices for work are 34% more productive than those who don’t. Using a device you’re comfortable with can make work more enjoyable, allow you to work flexible hours, and help you complete tasks more efficiently.
- Increases employee mobility: The days when employees left their desktop computers behind each afternoon are gone forever. The flexibility of BYOD allows employees to easily work from home or while traveling. Cell phones and other handheld devices have improved mobility even more than laptops since you don’t necessarily need a desk or a table (or even a chair) to use them.
- Potentially improves security: Can a BYOD program improve security? Most device users already have security features like screen locks or passwordless authentication enabled. They also tend to be protective of their own devices since the information they contain, and the devices themselves, are valuable. An effective BYOD policy and a strong company quality culture can help each employee enhance their own cybersecurity and that of the business, while a weak or inappropriate policy might be disregarded or become counterproductive.
48% of surveyed organizations expect BYOD adoption to increase.
The challenges of BYOD
Despite the long list of benefits, BYOD also introduces security risks based on a lack of company control over device use, location, and protection. These limitations can lead to expensive consequences if inadequate controls or unclear policies lead to data breaches, compliance issues, or malware that spreads to the company network. A thorough BYOD company policy should address the risks and challenges of remote work and personal devices such as:
- Mixing of personal and company information. Employees using devices for both personal and work purposes is the greatest challenge of BYOD. Unless employee tracking is used, IT won’t have visibility into the websites an employee visits, the apps they download, or the WiFi networks they connect to, which are among the many factors contributing to increased security risk.
- Less control over acceptable use. Your company may already have an acceptable use policy covering work email, internet browsing, network access, and VPN use. This policy can be extended to include BYOD issues as well. Important usage concerns include company data storage on personal devices and password security requirements. Acceptable use policies for BYOD must also account for activities that happen outside of the workplace, including:
- Malicious apps and websites are a constant security threat when downloads and browsing aren’t restricted. Some malicious apps disguise themselves as cameras or messaging apps to intercept sensitive information. Malicious websites can harbor malware and other security threats. Other apps and websites have no malicious intent but still increase risk due to poorly designed security features.
- Unsecured WiFi poses a risk to BYOD users and their employers when hackers exploit unsecured public networks to intercept data using tactics like man-in-the-middle attacks. Using a virtual private network (VPN) should be mandatory in these instances. A VPN protects business and personal information by encrypting data and routing all communication to and from the device through a secure portal.
- Lost or stolen devices. Since BYOD devices are frequently transported and used outside company walls, they’re more likely to be lost or stolen. Wiping the device or resetting the password remotely can help minimize the impact. The BYOD policy should clearly spell out the reporting process and other immediate actions to be taken when a BYOD device is lost or stolen.
- Employee responsibility for password management. In the absence of BYOD policies for organizations, workers might create weak passwords, reuse passwords frequently, or use unsafe storage methods like browser password managers. To reduce the effectiveness of hacking, the company and employee should share responsibility for BYOD password hygiene, including the mandated use of a secure password manager.
How to create the right BYOD policy
Employees who choose to participate in BYOD programs need to understand their rights and responsibilities, and putting a written policy in place is the first step. Creating the right policy doesn’t mean copying and pasting a sample BYOD policy from the internet. Effective BYOD policies for organizations are customized to suit the company’s mobility, culture, and security needs. Here are some things to keep in mind:
- Consider the scale of your business. A smaller business might only need a blanket policy to cover general requirements, whereas a larger enterprise might need to include more device types and authentication practices. Employee onboarding and departure policies for BYOD might also be more relevant for large or fast-growing companies.
- Consider the industry. The security, privacy, and legal issues surrounding BYOD policies will vary according to the industry. For example, in healthcare, where private and sensitive information is collected, the BYOD policy should emphasize elements like 2-factor authentication, VPN use on external WiFi networks, and data-wiping processes for lost or stolen devices to ensure compliance with HIPAA regulations.
- Evaluate how dramatically the change will impact business. How will the BYOD company policy be received? If employees are already using personal devices for work purposes, will they find new guidelines restrictive? A clear policy defining acceptable use, ownership, and security practices might even encourage more employees to participate, but the impact on the business should be reviewed in advance.
- Determine the desired level of IT control. The restrictions, monitoring practices, and security software requirements you establish should be based on the value of your company data and the potential impact of hacking and data breaches. Organizations that collect and maintain sensitive customer information like financial or health records need a higher level of IT involvement in the BYOD program, which needs to be described in the policy.
- Decide which devices are permitted. The choice between full, COPE, and hybrid BYOD policies is partly driven by the types of devices and operating systems you choose to allow. COPE policies give employees limited options for device types. Full BYOD policies leave the choice up to the individual, which can make software updates and compatibility issues more challenging for IT teams.
BYOD policy best practices
Although the scope and focus of the policy will vary depending on the business, a few BYOD security best practices should always be followed:
- Establish device security requirements. There‘s no room for exceptions when it comes to minimum device security requirements. The use of a VPN, device security apps, 2-factor authentication (2FA), and Identity and Access Management (IAM) solutions should be clearly described in the BYOD policy and strictly enforced.
- Clarify device ownership. BYOD policies where employers don’t purchase the device can blur the ownership lines, especially when stipends are provided for existing devices. Ownership definitions need to be clarified upfront to avoid confusion over device replacement responsibilities and device and phone number ownership when employees leave the company.
- Specify password management requirements. Using a business password manager can mitigate BYOD risks by ensuring strong passwords are generated, maintained, and protected by encryption. The BYOD policy should include the password management software used and guidelines for safe password storage and sharing.
- Communicate with your employees. Consider communicating the BYOD policy and its purpose during the drafting process rather than waiting until implementation. Employees might have their own useful BYOD policy examples and preferences to share if plans are communicated earlier. An effective training program to communicate and implement the final BYOD policy is also essential.
- Document your BYOD policy. Each BYOD policy should be tailored to the organization’s specific industry, security requirements, size, and mobility. Most BYOD policies include the following elements, at a minimum:
- Antivirus software requirements
- Usage restrictions
- Data privacy rules
- Company stipend
- Lost and stolen device process
- Employee termination process
How Dashlane helps you implement your BYOD policy
Standard Dashlane features, including 2FA and VPN, help reduce the vulnerability and inconsistency of BYOD programs. A Password Health score that tracks weak, reused, and compromised passwords allows employees to stay engaged in the company security culture and improve their password hygiene, even while they travel or work from home.

Separate Business and Personal spaces support the BYOD working style by allowing employees to separate business and personal passwords on their laptop or mobile device while protecting each category. This feature also allows businesses to monitor the entire organization’s Password Health while maintaining employees’ privacy. Including Dashlane in your BYOD policy is a great way to ensure every employee has the security tools and protection they need.
A good password policy strengthens your organization’s security culture, reduces the chances of a data breach, and balances security with employee needs. Find out how to create an effective password policy for your organization.
References
- Dashlane, “How Businesses with a BYOD Policy Can Secure Employee Devices,” January 2023.
- Zippia, “26 Surprising BYOD Statistics,” October 2022.
- Dashlane, “3 Remote Work Security Practices for Your Small Business,” October 2022.
- Dashlane, “Why Do You Need a VPN? Don’t Miss These 3 Key Benefits,” August 2020.
- Dashlane, “How Admins Can Simplify Provisioning,” April 2022.
- TechTarget, “COPE (corporate-owned, personally enabled),” May 2021.
- Stater Story, “How Much Does Technology Equipment Cost For My Business?” October 2022.
- Voxer, “6 Advantages Of BYOD And How It Increases Productivity And Profits,” July 2019.
- Dashlane, “What is Passwordless Authentication, and Why Should You Care?” November 2022.
- ScienceDirect, “Malicious Apps,” 2017.
- Dashlane, “Why Employees Shouldn’t Let Browsers Save Their Passwords,” March 2021.
- Dashlane, “Why Choose Dashlane Business?” March 2022.
- GP Meridian, “How to Compliantly Onboard and Offboard Remote Employees,” August 2022.
- Dashlane, “Data Breach or Hack? Know the Difference,” June 2021.
- Compliancy Group, “What is HIPAA?” 2023.
- Dashlane, “Why Financial Services Need a Password Manager,” November 2021.
- Dashlane, “Healthcare Providers: Focus on Patients While Dashlane Deals With Your Passwords,” August 2022.
- Dashlane, “Creating a Password Policy Your Employees Will Actually Follow,” July 2022.
- GetVoIP, “What is BYOD? Complete Guide to Bring Your Own Device,” March 2023.
- Digital.AI, “Best Practices for Employee BYOD Training,” 2023.
- Gartner, “Identity and Access Management (IAM),” 2023.
- Dashlane, “Secure Business Password Manager,” 2023.
- Dashlane, “Everything You Need to Know About Your Password Health Score,” October 2020.
- Dashlane, “How to Safeguard Sensitive Data for Businesses,” 2023.
Sign up to receive news and updates about Dashlane
