Dashlane to leverage confidential computing for secure passkey storage and sharing
Signing in to services with a passkey is both convenient and secure. Unlike passwords, passkeys are always unique and strong—and, critically, they’re phishing-resistant.
With Dashlane’s passkey management tool, users can create and store passkeys and easily use them across different platforms. While Apple and Google have provided APIs that allow passkeys to be managed on iOS, macOS, and Android, the Windows platform has, until recently, lacked such APIs. Due to the popularity of browser extensions, Dashlane implemented passkey support directly into our extensions.
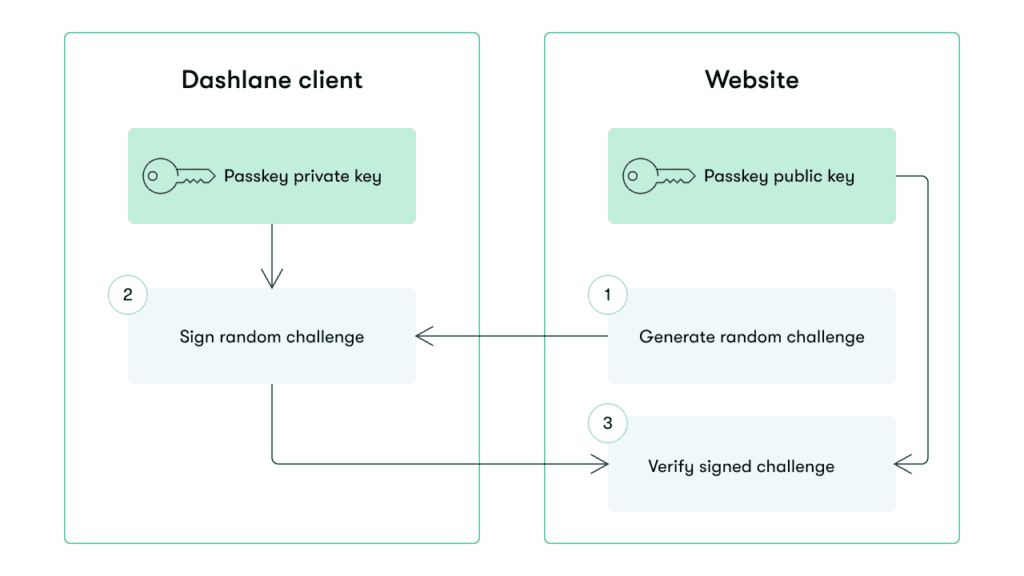
Passkeys use public key cryptography. When passkeys are stored in Dashlane, the private key is securely encrypted in the Dashlane vault, while the public key is stored with the service associated with the credential. When a user signs in with a passkey, the service creates a random challenge that is sent to the user’s device, and the private key is used to sign the challenge, which is then returned to the service and verified using the public key. Today, the passkey is handled in the memory of the Dashlane client, but we’ve been considering how we can make this more resilient from a security perspective.
AWS Nitro System
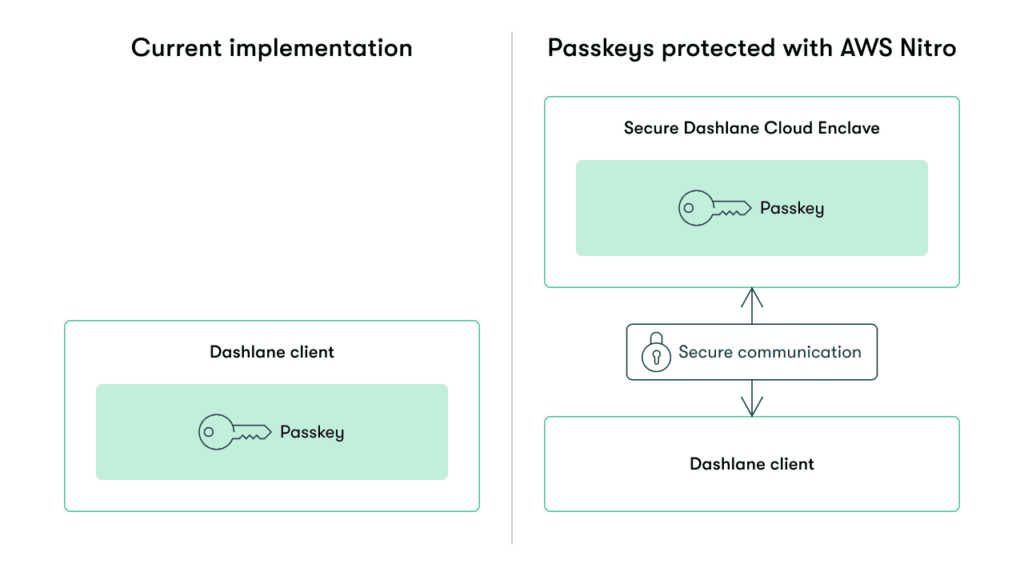
Dashlane uses confidential computing and secure cloud environments, including the AWS Nitro System, for capabilities such as signing in with SSO. With this knowledge and experience, we’re making passkey usage even more secure. We’ve started working on a solution where, instead of the passkey being decrypted directly within the browser extension, it would be decrypted within an environment such as the AWS Nitro System. This way, the private key’s protection is much more dependable, enhancing overall security. In both cases, the user is always in possession of the encryption keys, and confidentiality is maintained.
Secure passkey sharing
Businesses often need employees to securely share credentials. Sending passwords using email or messaging platforms exposes those credentials to malicious actors, so these unsecure credential-sharing methods should be avoided.
Dashlane users can share credentials securely using public key cryptography. You can think of sharing credentials as a way of handing over copies of keys, just as you would with your house key. Sharing your house key carries the risk that the borrower might cut copies of the shared key. Passwords carry the same risk because they are typically shared by value—the password’s value is handed over to someone else.
Passkeys protected with AWS Nitro facilitate sharing by reference rather than by value. This means the passkey doesn’t need to be given away in order to be shared. The passkey will only be shared with those who need access to it. In addition, use of that passkey will always be auditable because each use is guaranteed to be logged for auditing purposes. Businesses cannot do this with passwords because a password is a simple value that is shared with the website server to authenticate the user. Since passkeys use public-key cryptography, monitoring and security are inherently much more robust.
Beta coming soon
Want to try this new passkey capability? A beta version will be available by the end of the year, and the feature will be generally available in 2025.
Get the latest news on passkeys at Dashlane by subscribing to our newsletter or joining our Reddit community.
Sign up to receive news and updates about Dashlane