One of the Most Common Data Breaches Your Organization Can Prevent with One Step
Eliminating reused passwords is the simplest form of defending against cyber threats.
Navigating cybersecurity is no easy task in today’s digital environment. But it doesn’t all have to be complicated. Reused passwords are one of the most common root causes behind data breaches. And a simple way to address it is by preventing your employees from recycling passwords.
Your employees are moving at a million miles an hour, always looking for shortcuts that boost their productivity. Unfortunately, when that includes reusing their passwords, they’re also creating a shortcut for cybercriminals into your company.
Certainly, creating unique passwords for every account is no one’s idea of a productive time. Especially since employees have dozens of work-related accounts these days. That’s where tools like Dashlane come in—uncomplicating the task of creating and using complex passwords so employees don’t even have to stop and think about it.
Want to learn more about using Dashlane Password Manager at home or at work?
Check out our personal password manager plans or get started with a free business trial.
Don’t think one recycled password can hurt you?
Just ask Colonial Pipeline, whose operations were crippled after a ransomware attack (which cost $4.4 million in ransom alone).
Or consider SolarWind, whose breach had massive implications(the latest: stolen U.S. counter-intelligence documents).
Both these incidents began with attackers gaining initial access via employee credentials. In both cases, security researchers found those passwords on the dark web—indicating the strong likelihood that those employees reused passwords from previous, unrelated data breaches.
As extreme as the Colonial Pipeline and SolarWind examples may seem, reused passwords are far more common than you may realize. In 2021 , Spycloud found that among people who had more than one password stolen, 60% of credentials were reused across many different accounts. Do you know how many of your employees are doing the same?
Why cybercriminals love reused passwords
Cyberattackers typically follow the same pattern when they try to hack into a network. And based on the latest research by Verizon for its annual Data Breach Investigations Report (2022), we know that 50% of confirmed data breaches involve user credentials. From hackers’ standpoint, it’s simple: Why should they break in when they can log in?
Credential stuffing is one common way for cybercriminals to put recycled passwords to good use. With the help of automated scripts and botnets, they can test a large batch of compromised credentials obtained from the dark web to see if they work on another site.
While the success rate of credential stuffing login attempts is low, the end result can be quite significant based on the sheer number of attempts. For example, Verizon found that many organizations experienced hundreds of thousands of credential stuffing attempts—and some as many as 3.3 billion!
One successful example is Zoom, which had half a million of its user account credentials exposed on the dark web last year. Zoom itself wasn’t hacked—the likely culprit was credential stuffing.
Reused passwords and the risk of a ransomware attack
The fact that a reused password was likely involved in the Colonial Pipeline attack is not surprising. Like your employees, cybercriminals, too, are looking to cut corners and improve their efficiency. On the dark web marketplace, that translates into ransomware gangs outsourcing many tasks to ransomware-as-a-service providers that specialize in delivering specific services—for a fee, of course.
Among the various services that ransomware operators typically outsource is the initial access into the targeted organization. Specialists called initial access brokers do nothing else but find and sell those entry points. They can find this access in a number of ways, but compromised credentials are often the fastest and most effective tactic (another shortcut!), with Remote Desk Protocol (RDP) and virtual private networks especially a target.
Recently, security researchers noted a spike in demand for initial access broker services. Another researcher group was tracking around 500 marketplaces selling initial access, with the average price a little over $7,000 and nearly $10,000 for RDP access.
What does all this mean for your organization?
Surveys show that employees don’t think twice about recycling passwords. In a study we conducted with Harris Poll, we found that only 26% of 1,200 surveyed employees felt guilty about reusing passwords for multiple accounts. A study by Specops Software found similar results: 45% of more than 1,300 respondents didn’t think password reuse was a serious issue.
To prevent employees from reusing passwords, you can do three things:
- Change your security culture so employees understand that reusing passwords is a big deal—and why.
- Provide employees the tools that make it easy and simple to maintain good passwords habits like using only unique, complex passwords.
- Enable them to change compromised passwords proactively.
Dashlane can help you do all three.
How Dashlane can help
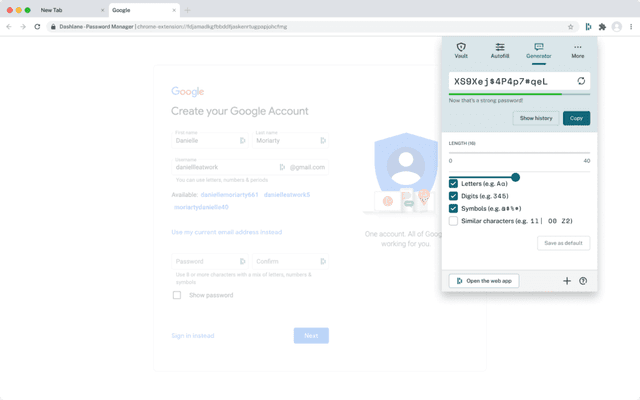
Password Generator
Employees can quickly create random, unique, complex passwords with Dashlane’s random password generator—whether they need a replacement for a compromised password or a login for a new website or app. We’ve recently improved this feature to make it more customizable, convenient, and secure. And with our autofill (also recently improved with machine learning), we enable employees to not only login but also check out and fill out a web form with only one convenient click.
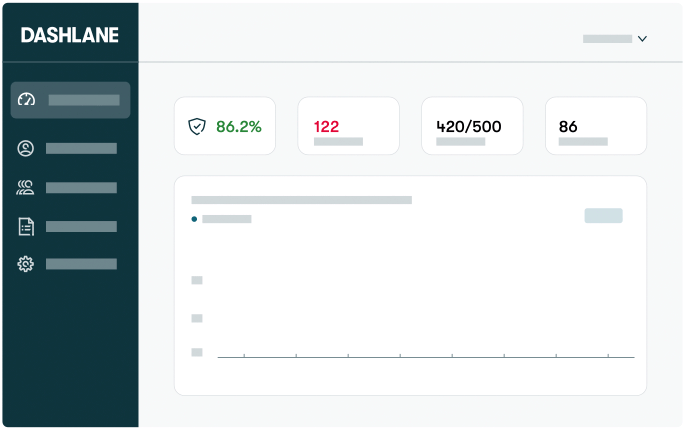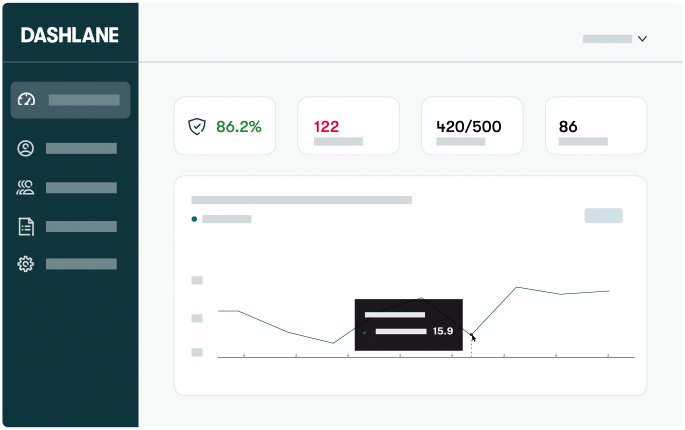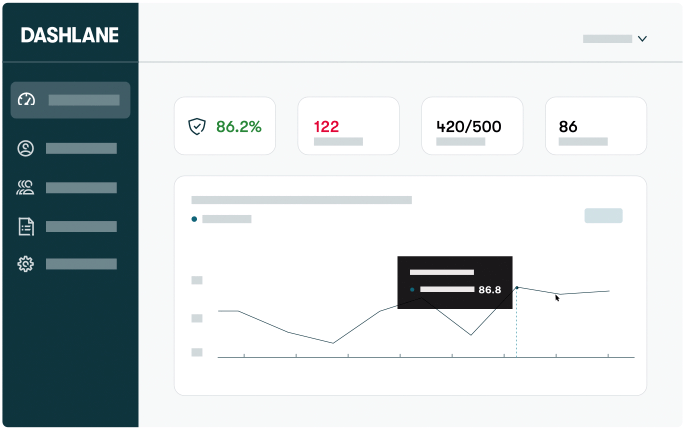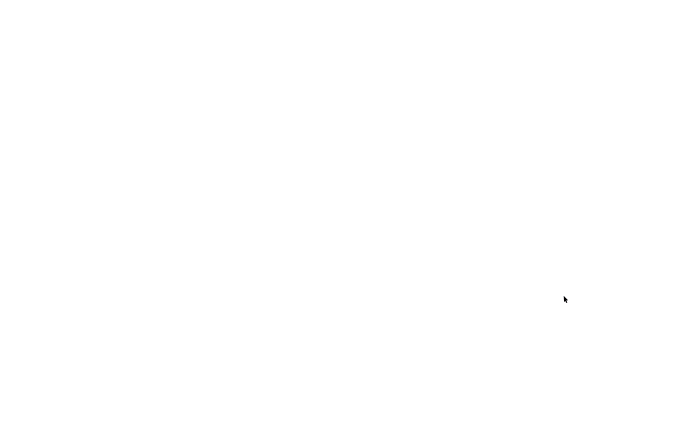
Password Health
With Dashlane’s Password Health Score, you can benchmark company-wide security scores, track progress over time, and identify risky employees—so you can engage them in conversations about security and password best practices.
Dark Web Monitoring
Dashlane’s Dark Web Monitoring feature scans billions of user credentials on the dark web, updating the data daily. When the app finds that an employee’s monitored credentials have been exposed, it sends an immediate alert and prompts the employee to change the password.
Yes, cybersecurity is complex. Yes, you need multiple layers and tactics. But why not take advantage of something as simple and effective as banishing reused passwords. Good password hygiene makes cybercriminals’ job that much harder—and makes you a much less appealing target.
Want to learn more?
Ready to get started. Sign up for a free business trial.
Sign up to receive news and updates about Dashlane
