What is DNS Cache Poisoning or DNS Spoofing?
As an IT or business professional, you can enhance your organization’s cybersecurity by understanding DNS cache poisoning. According to the IDC 2023 Global DNS Threat Report, the organizations surveyed suffered an average of 7.5 DNS attacks per year.
Whether it's an e-commerce site or a secure database, these attacks can lead to costly ramifications. In this post, we'll explore what DNS cache poisoning means, break down how it happens, and provide you with actionable strategies to shield your organization's systems.
Want to learn more about using Dashlane Password Manager at home or at work?
Check out our personal password manager plans or get started with a free business trial.
What is DNS cache poisoning?
DNS cache poisoning—also known as DNS spoofing—is a cybersecurity attack that inserts incorrect Domain Name System (DNS) information into a DNS resolver cache, directing users to unintended and potentially malicious websites.
Here's a simple way to understand it:
- Domain Name System: The DNS uses a variety of servers to translate website domain names into IP addresses. It's like a phone book for the internet.
- DNS resolver cache: This is a temporary database maintained by a device’s browser, operating system, router, or internet service provider (ISP). It stores DNS lookups from recent visits to websites, so your browser doesn't have to find the information again.
- DNS cache poisoning: When this cache gets incorrect information (either accidentally or maliciously), visitors can be directed to the wrong sites.
A DNS spoof attack is about incorrect information in a system that usually helps your device, such as a laptop or smartphone, find websites fast—it doesn't mean there's something wrong with your device or the websites themselves.
By understanding what DNS client cache poisoning is and how it works, users and website administrators can take proactive steps to lessen their chances of being affected.
How do DNS poisoning attacks work?
When DNS client cache poisoning occurs, the request to visit a particular website can be redirected to a malicious site instead of the intended one. This fraudulent site may look exactly like the genuine site, leading people to believe they're in the right place. Here's a simple breakdown:
The normal process:
- You type a domain name into your web browser and it asks a DNS server for the IP address of the website.
- The DNS server looks up the address and sends it back.
- Your device stores this information in its DNS resolver cache for later use.
The attack:
- An attacker puts false information into the DNS resolver cache.
- They might manipulate a vulnerable DNS server or trick your device using man-in-the-middle or phishing techniques.
- The incorrect information redirects you to a different website that might look the same. In reality, the attacker controls the website, putting you at risk.
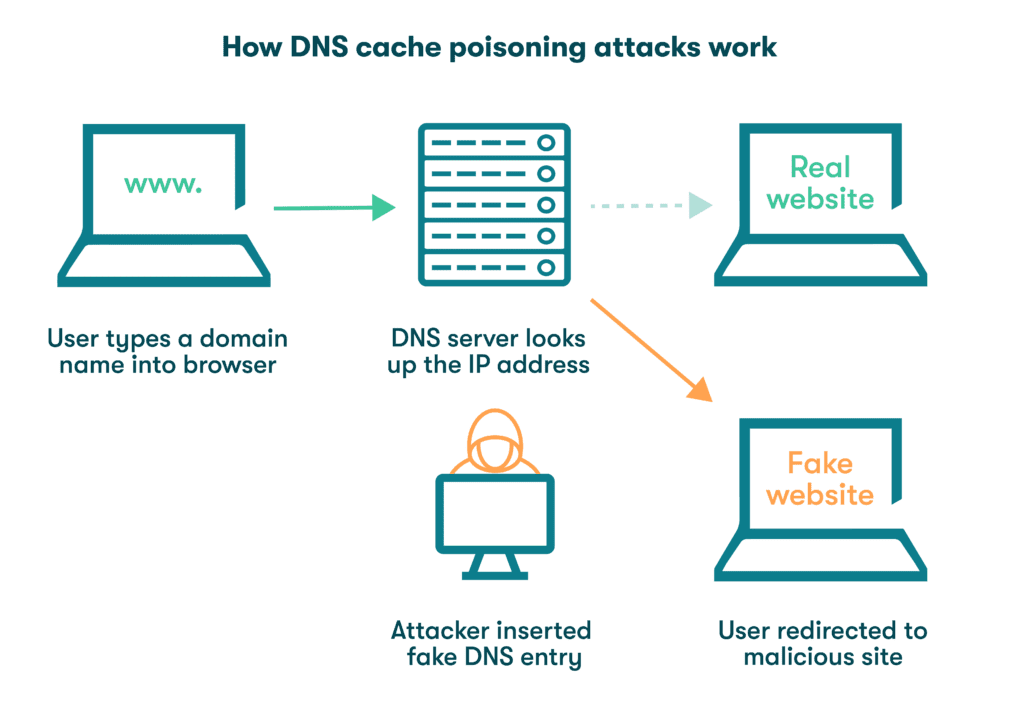
Until the cache expires, someone trying to visit a legitimate website might end up on the attacker's site without even realizing it. They might enter sensitive information or download malware, thinking they're on a site they trust. Fortunately, awareness of how DNS poisoning attacks work empowers you to take actions that lower the risk and help you and your organization stay safe online.
Consequences of a DNS spoof attack
Understanding the potential outcomes of a DNS cache poisoning incident is the first step toward protecting your organization. Let's look at some of the consequences that can be prevented by protecting against DNS attacks.
Sensitive information exposure
Cybercriminals can capture information entered on a malicious site. This data may include names, passwords, credit card numbers, and addresses,, for example. Beyond exposing sensitive information and intellectual property, data breaches shake the trust and retention of employees, investors, clients, and vendor partners.
Financial loss
Both your business and your customers can incur monetary losses when cybercriminals use stolen information or deceive consumers into making payments on fake sites. Remember when Google and Facebook paid fake invoices for years totaling $122 million? For businesses, the cost impact snowballs as they address the breach, notify affected customers, and deal with potential penalties and lawsuits.
Reputational impact
A DNS attack can wreak havoc on an organization’s public image. If people lose confidence in a site because they were once redirected to a malicious one (or worse, their information was compromised), they will hesitate to use it in the future. Public relations and risk management teams must work proactively and strategically to manage the fallout and rebuild trust with current and future employees, investors, and customers.
“Our strongest [business] tools are our reputation and relationships.”
Principal, Vice President at JD+A
Who are the common targets of these attacks?
DNS cache poisoning doesn't discriminate. Understanding the typical targets can help organizations be proactive. Here's a look at a few of these common targets:
- Individuals: Everyday internet users, even careful users, can be affected without the right safeguards.
- Small and medium businesses: Businesses without dedicated IT teams or robust security measures. A threat actor might see them as an easier target, but that doesn't mean they're defenseless.
- Large corporations and government entities: Even those with strong security protocols can be susceptible. The potential rewards for threat actors may be greater, but so are the defenses.
No one's immune to a DNS spoofing attack. Whether you're working from home, running a small business, or managing IT for a large organization, you can take action if you understand the risks.
5 ways to mitigate the risk of a DNS poisoning attack
Preventing a DNS spoof attack is all about being proactive and using the right tools and knowledge. Here are five practical ways to reduce the risk:
- Enforce HTTPS connections. An effective and practical way to prevent DNS poisoning attacks is to enforce HTTPS connections by deploying HTTP Strict Transport Security (HSTS). HTTPS is a secure method of sending encrypted data between a browser and a website. Configuring your web server for HSTS tells browsers to only access your website using secure HTTPS connections. The HSTS preload list simplifies the communication between web servers and major web browsers (such as Chrome and Firefox) by preloading a list of HTTPS-only websites.
- Consider DNSSEC (Domain Name System Security Extensions). DNSSEC adds an extra layer of verification to DNS responses using public-key cryptography and end-to-end encryption. It's like a tamper-evident seal on your mail—you'll know if something's amiss. However, DNSSEC is in its infancy and implementation is complicated and costly, placing it out of reach for many organizations.
- Securely configure your DNS. This step helps ensure the DNS queries and responses you're receiving are legitimate and haven't been tampered with. By enabling secure configurations, such as source authentication, you're adding another layer of verification, akin to having a security checkpoint for your online destinations.
- Educate employees on browser settings. Train employees to set their browser settings to HTTPS-only mode across all their devices. Further, if the browser ever displays a warning that the SSL/TLS certificate is invalid, they shouldn’t visit the site. This warning could mean the DNS cache is compromised, but since the hacker doesn’t have the original SSL certificate for the website, the browser can’t verify the identity of the website owner.
- Encourage employees to always use a VPN. A virtual private network (VPN) encrypts an internet connection, ensuring the employee’s data travels securely between their device and the websites or services they’re accessing. Ideally, the VPN can also manage the DNS cache rather than trusting the local router.
Being targeted doesn't mean being a victim. Taking proactive measures like these helps fortify your organization’s digital space, making it a safer environment for all stakeholders and operations.
Steer clear of DNS cache poisoning
DNS cache poisoning might seem technical, but it doesn't have to be a tangled web.
As a business or IT professional, you now possess knowledge of what DNS spoofing is, an understanding of how it happens, and tools to prevent these attacks. With these insights, you're not only safeguarding your digital assets, but also contributing to a more secure online environment. For these benefits to trickle down to all employees, consider using human-centric security tools and policies to innately drive behavior change. A credential manager with user-friendly single sign-on, secure autofill, and a VPN makes it easy for employees to contribute to your organization’s cybersecurity efforts.
Learn about all the ways Dashlane secures data and guards against potential attacks in our Security Principles & Architecture white paper.
References
- EfficientIP, “IDC 2023 Global DNS Threat Report,” 2023.
- Cloudflare, “What is DNS?”
- Dashlane, “11 Cyber Threats To Be Aware of & Defend Against,” April 2023.
- KeyCDN, “Quick Guide to DNSSEC,” 2023.
- Keyfactor, “What is DNS Poisoning? (aka DNS Spoofing),” February 2021.
- GeeksforGeeks, “DNS Spoofing or DNS Cache poisoning,” 2023.
- Consumer Reports, “Set Up HTTPS-Only Mode on Your Browser.”
- Cloudflare, “What is an SSL certificate?”
- Dashlane, “A Complete Guide to Multifactor Authentication,” November 2022.
- Dashlane, “Benefits of Artificial Intelligence in Cybersecurity,” December 2023.
- Dashlane, “Why You Should Keep Your Apps Updated,” March 2022.
- Dashlane, “How to Create a Culture of Security,” March 2022.
- Dashlane, “Why Do You Need a VPN? Don’t Miss These 3 Key Benefits,” December 2022.
- Dashlane, “What Is Ethical Hacking & Why Is It So Important for Cybersecurity?” December 2023.
- Dashlane, “5 Recommendations to Kickstart Your Cybersecurity,” August 2022.
- Dashlane, “What the Hack Is Malware?” February 2020.
Sign up to receive news and updates about Dashlane
