A Guide To External Security Threats in 2024
In today’s ever-connected world, the number of devices and accounts we need to manage keeps increasing. All this digital activity creates opportunities for cybercriminals to take advantage of weaknesses. While we may be subject to internal security threats at work or on the go, the list of external security threats is also expanding quickly.
Defining external vs. internal security threats
Security issues can be divided between internal and external cybersecurity threats. Before we dive into some external threat examples, let’s take a look at what an external threat entails and how it differs from an internal threat.
External threats
External security threats include many categories that originate from outside company walls and are initiated by someone with no affiliation to the business. External threats can also be directed at individuals. Hacks or schemes to steal passwords and online scams that convince us to share credentials willingly are directed at both personal and business accounts. External risks also include physical threats like device or network tampering intended to disrupt operations.
Internal threats
The word internal typically refers to threats within the workplace. Internal threats are only a concern for businesses and their employees. Common internal threats that IT teams contend with include:
- Disgruntled employees who tamper with or destroy data or devices. This can also include contractors or vendors with malicious intent who have direct access to company systems and files.
- Ex-employees who retain their credentials and use them to inflict damage on company assets.
- Bring your own device (BYOD) practices that allow employees to transfer malware and other cybersecurity threats from their private files to the company network.
“Our employees are our greatest asset, but we discovered they were also our biggest security threat.”
Senior VP of Technology, ePromos
Want to learn more about using a password manager for your business?
Check out Dashlane's business plans or get started with a free business trial.
The different types of external cybersecurity threats
Improved technology and connectivity have redefined our online experience, enabled remote working and BYOD practices, and given us more device options. Unfortunately, these changes also give cybercriminals more endpoints to exploit and more ways to gain entry and inflict damage.
Cybercriminals
A cybercriminal is someone who uses their skills to steal information or hijack computer systems for financial gain. Some choose to buck the stereotype of the lone cybercriminal by working as part of an organized team or squad. The growing list of hacking practices used to pull off external attacks includes:
- Phishing: A phishing attack, often in the form of an unsolicited email, attempts to trick the recipient into sharing their account information or passwords. Some also include links to unsafe files or websites. Poor grammar and URLs that do not match the company website can be signs of a phishing email, but these signs are not always present—phishing and social engineering tactics are growing ever more advanced.

- Brute-force attack: This common hacking tactic uses random combinations of usernames and passwords to attempt an account login until a match is found. Artificial intelligence and automation allow cybercriminals to execute these attacks more easily. Reusing passwords increases vulnerability to this type of external attack since the bad actor can use those same credentials to access multiple accounts.
- Man-in-the-middle attack: An MitM attack is often attempted in areas with unsecured WiFi connections, like airports and hotels. Although this type of attack is relatively rare, cybercriminals canintercept communications or redirect people to fake websites to steal their information. A VPN reduces the threat of MitM attacks by encrypting all data going into or out of a device and routing it through a secure portal.
- Denial-of-service attack: This form of cybercrime, usually directed at businesses, uses automation to overwhelm a website with traffic until it eventually shuts down. A distributed denial of service (DDoS) attack uses the same approach, with the flooding traffic originating from multiple sources, making it difficult to block.
- SQL injection: A structured query language (SQL) injection uses malicious code to trick a database into displaying information that was not intended to be exposed. This sophisticated external threat requires the hacker to study their target carefully and identify vulnerable apps from which to launch their attack.
- Zero-day attack: When new software packages or updates are released, there may be vulnerabilities or flaws that can be exploited if they are noticed before the developer can correct them; zero-day refers to this release date. A cybercriminal will attempt to use tactics like phishing attacks to evade external website security and infiltrate the system before the software bug is fixed.
- Dead man’s switch: The concept of a dead man’s switch originated with automatic railroad stops that triggered when the engineer became incapacitated. Hackers and cyberterrorists have given the dead man’s switch new meaning by setting up cyberattacks that automatically launch when they fail to log in or take other specific actions.
- Drive-by attack: Another term borrowed from the pre-digital age, a drive-by attack hides malicious programs on seemingly harmless links or websites. If someone unknowingly clicks on one of these links, malware is automatically installed onto their device without their knowledge.
- Spoofing: As the name implies, spoofing or “evil twin” attacks trick unsuspecting users into logging on to an illegitimate WiFi network by assigning it a name similar to an actual public WiFi network. Once someone logs onto the spoofed network, their personal data can be intercepted and stolen by the hacker.
Malware
Malware, short for malicious software, can describe any type of intrusive software that is intended to steal data, damage hardware, or otherwise interfere with a computer’s normal functioning. Common malware types are spyware and ransomware. While some malware attacks are simply intended to annoy us, other forms are designed to steal data or make computers and devices unusable.
- Spyware: This dangerous form of malware installs itself on your device and begins monitoring your activity and relaying it back to the cybercriminal. Difficult to detect, spyware can be used to collect personal information like your passwords and credit card numbers.
- Ransomware: This form of malware is used to hold a device or an entire network hostage by preventing companies or individuals from accessing their own files until a ransom is paid, typically using a credit card or cryptocurrency.
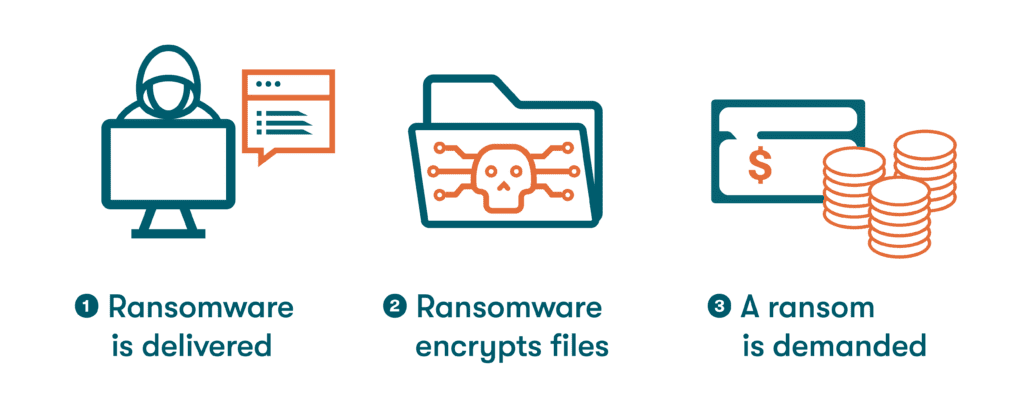
Slow computer performance, unexplained pop-ups, and unusual changes to browser or security settings are warning signs of a malware attack. If you or your employees suspect your computer or device has been hampered by malware, always work with an IT professional to secure the device, eradicate the threat, and change any potentially compromised passwords immediately.
The future of external security threats
Rapidly evolving artificial intelligence (AI), machine learning (ML), and automation tools are allowing hackers to crack passwords more strategically and efficiently. These tools also enable viruses and algorithms to quickly adapt as they learn from what they encounter and change without human intervention.
Security professionals will also benefit from this new technology, with signature patterns of malware identified more quickly and advanced analytics used to detect and fix software vulnerabilities before they can be exploited.
6 ways to prevent external security threats
Luckily, there are many advanced tools and practices that can protect us from external security threats. These options help to safeguard our privacy, data, and company property:
- Use data encryption
The process of data encryption provides protection from external attacks by scrambling passwords and other information into an unreadable format. For example, the Dashlane password manager utilizes AES-256 encryption, widely accepted as the strongest encryption type available, to protect your private information.
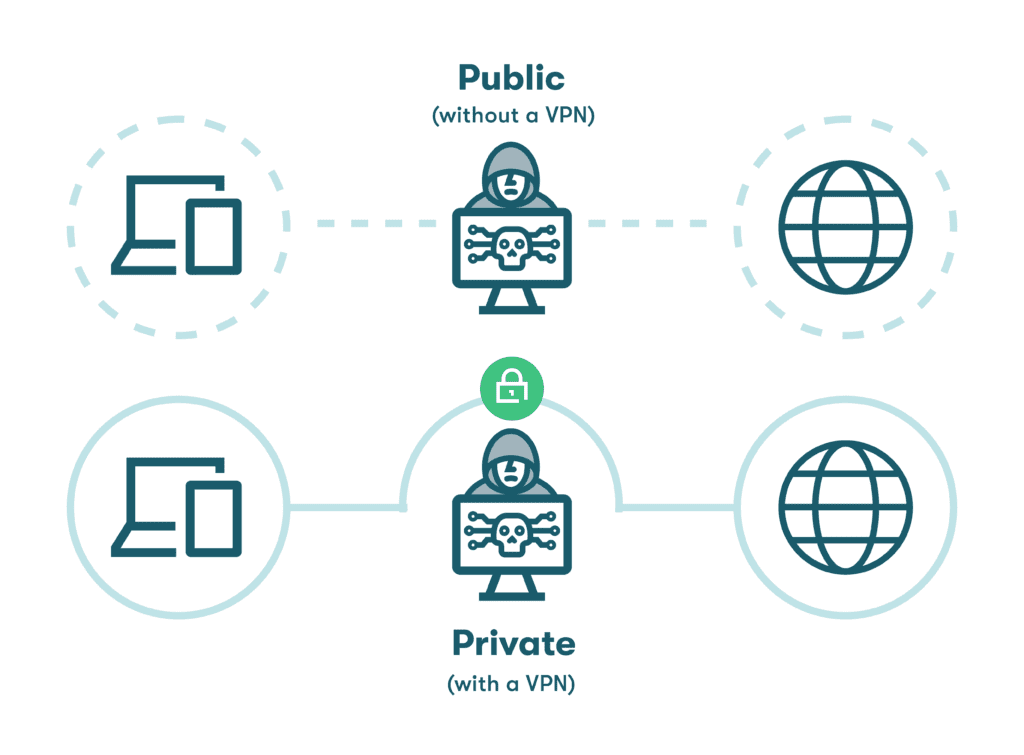
- Use a VPN on public WiFi networks
Public WiFi networks found in airports, cafés, and malls have the potential to be subject to hacking tactics like spoofing and man-in-the-middle attacks designed to intercept your information. When you join a public WiFi network, you should always use a VPN to encrypt inbound and outbound transmissions.
- Use 2-factor authentication
2-factor authentication (2FA) provides additional security by requesting a second login identifier, such as a unique code sent through an app or text message. This might add a few seconds to your login time, but it also makes it nearly impossible for an intruder to access your accounts without having your device in their possession.
- Educate employees
Awareness is the key to prevention. Educating yourself and your coworkers on the latest internal and external security threats will lead to faster cyber threat response times and improved password health to counteract external threats targeting weak or reused passwords.
- Establish a strong security culture: Many employees want to be actively involved in the identification and prevention of external attacks. A security culture encourages this participation through strong and consistent cybersecurity tools, policies, and shared metrics.
- Special considerations for remote workers and BYOD: Thorough training is essential for remote employees who might be less connected to IT teams and security best practices. BYOD policies help to mitigate external security threats by defining what apps, software, and WiFi networks can be used with employee-owned devices.
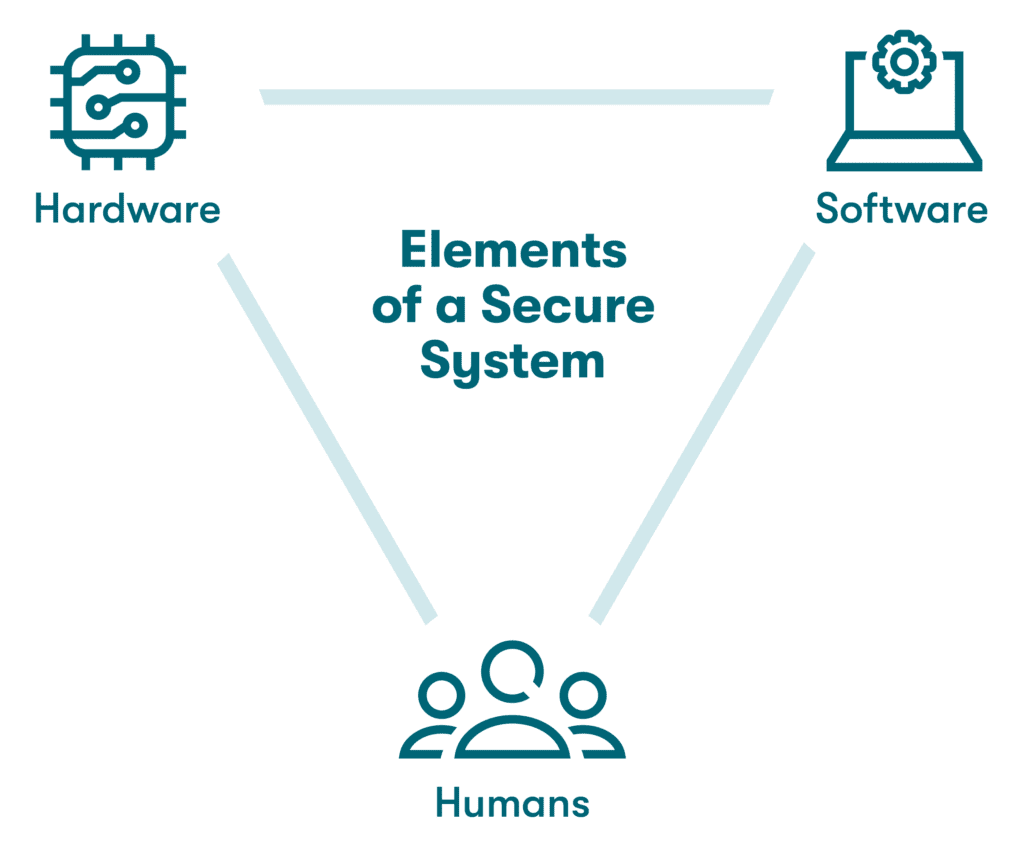
- Secure your system
Preventing and detecting all types of cybersecurity risks is easier when you deploy a variety of strategies to protect your company from cyberattacks. A secure system is made up of hardware, software, and well-trained employees working in concert to keep a company safe from cyberattacks and data breaches.
- Use the right tools
Powerful software tools help to protect you and your company from external security threats. Anti-malware and antivirus software packages are continually updated to detect the latest strains. A password manager improves security and efficiency by creating, protecting, and autofilling complex and unique passwords that make advanced hacking tactics less effective.
How Dashlane protects against external security threats
Dashlane provides intuitive password generation features with secure vaults for password storage and sharing that safely encrypt and protect all your data. Standard features, including AES-256 encryption, a Password Health score, and secure sharing, help you ward off external attacks. Our Dark Web Monitoring scans the depths of the internet for your credentials and alerts you if they have been impacted, while our patented zero-knowledge architecture ensures no one else can access your data—not even Dashlane.
External attack methods and the strategies to protect against them are continually evolving. Get a 360-degree perspective on the causes, consequences, and prevention of cyberattacks in our Business Guide to Data Breaches and Hacks.
References
- ITPro, “Smart devices more than doubled in US homes amid COVID pandemic,” June 2021.
- InformationWeek, “75% of Insider Cyber Attacks are the Work of Disgruntled Ex-Employees: Report,” July 2022.
- GovTech, “Hacked or Scammed?” July 2022.
- Microsoft, “What is an Endpoint?” 2023.
- Dashlane, “Happy Hour with a Hacker,” 2023.
- Dashlane, “Phishing 101: A Six-Step Action Plan,” 2023.
- Dashlane, “Why Do You Need a VPN? Don’t Miss These 3 Key Benefits,” August 2020.
- Microsoft, “What is a DDoS Attack?” 2023.
- Imperva, “SQL (Structured query language) Injection,” 2023.
- Makeuseof.com, “What Is a "Dead Man's Switch" and How Do You Set One Up?” July 2022.
- Norton, “What are drive-by downloads + drive-by attack prevention tips,” February 2022.
- Dashlane, “What the Hack Is Malware?” February 2020.
- Norton, “Spyware: What is spyware + how to protect yourself,” December 2021.
- Dashlane, “Always Change Your Passwords After a Breach,” March 2020.
- Dashlane, “What Is Encryption?” March 2019.
- Dashlane, “A Beginner’s Guide to Two-Factor Authentication,” August 2022.
- Security.org, “Do You Still Need Antivirus?” 2023.
- Dashlane, “Understanding your Dashlane Password Health Score,” October 2020.
- Dashlane, “How to Create a Culture of Security,” March 2022.
- Dashlane, “How Businesses with a BYOD Policy Can Secure Employee Devices,” January 2022.
- Dashlane, “What a Secure System Is & How to Implement It in Your Business,” October 2022.
- Dashlane, “A Step-By-Step Guide to Managing Passwords in Small Businesses,” January 2022.
- Dashlane, “Putting Security First: How Dashlane Protects Your Data,” January 2023.
- Dashlane, “Dark Web Monitoring: Your Employees Are Likely Using Compromised Passwords,” July 2022.
- Dashlane, “A Business Guide to Data Breaches and Hacks,” 2023.
- Dashlane, “Changing Passwords: Best Practices for Remote Workers,” March 2023.
Sign up to receive news and updates about Dashlane
