How To Make Sure Your Chrome Extensions Are Safe
Whether it’s installing a Chrome extension to block ads or using a Pomodoro timer for productivity, we use several Chrome extensions to personalize our browsing experience. While Chrome extensions and other browser plugins make web browsing easier, extensions can be used to track a user’s browsing activity and steal private data. In this post, we explore practical tips to make sure chrome extensions are safe.
What you can do to make sure your Chrome extensions are safe
Here are the best browser extension security measures to help ensure your Chrome extensions are safe.
Do your research
- Verify the developer’s legitimacy: To determine the safety of an extension, look for a professional developer with a public profile or website. If the website doesn’t have an HTTPS connection or you notice other suspicious elements like a vague privacy policy, it’s best to avoid installing that extension. You can also look for additional extensions made by the same developer. This will give you an idea of their experience and reliability.
- Check user reviews: Check user reviews to find dangerous extensions. See what others have to say about their experiences with the extension. If the extension has multiple negative reviews in the Chrome Web Store, try finding a similar version with better ratings. Remember, not all reviews are trustworthy, so watch out for fake or unhelpful ones.
- Make sure the extension is up to date: If the developer is actively maintaining and improving the extension, it's a good sign of its ongoing security and functionality. However, outdated extensions aren’t equipped with the latest security patches, making them vulnerable to cyber threats. If you encounter an extension that hasn't been updated in over a year, it's advisable to search for a more reliable alternative.
- Understand the risk of granted permissions: Whenever you install an extension, you have to grant certain permissions to access your data in order for it to work. Permissions can have a low, medium, or high alert risk level. The permission required for extensions is of low alert risk if it only requires access to organize other extensions, themes, and apps. On the other hand, a medium alert risk requests access to all your data on visited websites, while a high alert risk can access all your data, both online and offline.
These risk levels are subjective to each user. Before you grant permission, evaluate the risks and determine whether or not you should grant the respective permissions required by the extension. For example, in a work environment, you should evaluate the permission risk levels according to your organization’s security policies. - Check the source code: If you understand programming, you can make sure your browser extensions are safe by glancing through the extension codebase. You can view Chrome extensions’ code using the Chrome extension source viewer. This enables you to dig a little deeper and find malicious or risky code snippets intended to steal your data or track your activity.
Want to make life harder for scammers?
Check out our free username generator and random password generator tools.
Think you have a strong password? Use our password strength tester tool to put it to the test!
Be wary of browser extension red flags
To make sure your chrome extensions are safe, avoid installing any extensions that:
- Don’t verify the legitimacy of the developer.
- Have significant negative reviews or lack of reviews at all.
- Demand more permissions than required.
- Aren’t recently updated.
- Have unclear privacy policies.
Install anti-malware and use a VPN
It’s a good idea to install anti-malware software before adding extensions to your browser. Such software can keep track of all the incoming data to your browser, including extensions, and alert you if malicious code is detected.
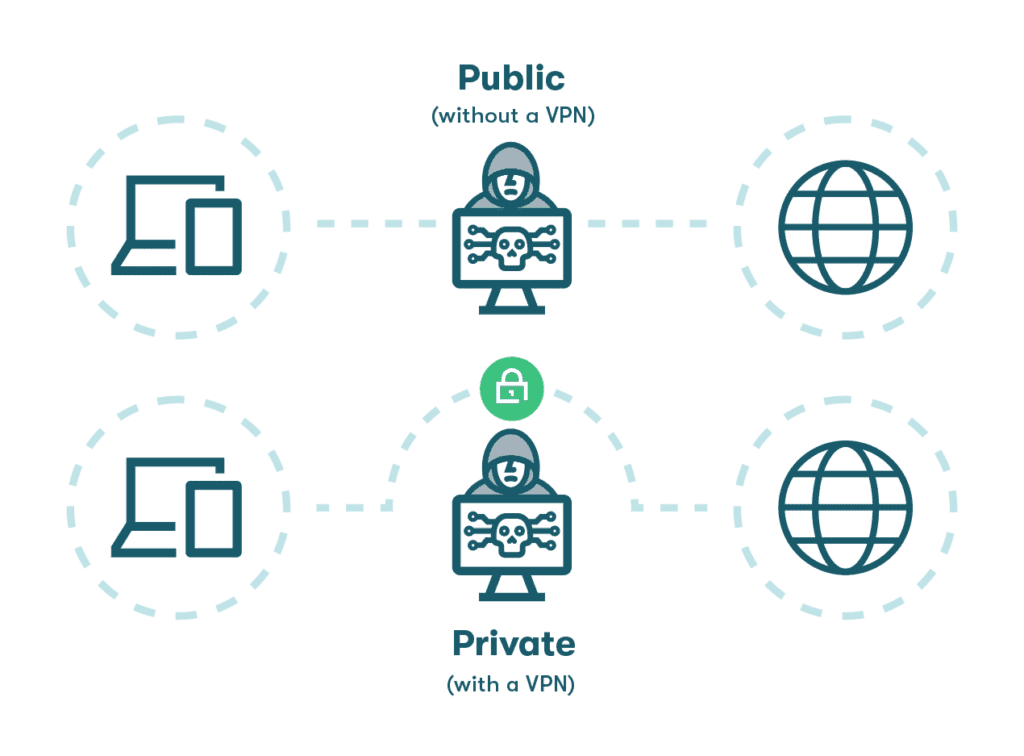
You can further increase your browser extension security by using a virtual private network (VPN). A VPN encrypts your online data and masks your identity. It's especially important to use a VPN when connected to public, unsecured WiFi networks, such as at an airport or a coffee shop.
Find trusted extensions to install
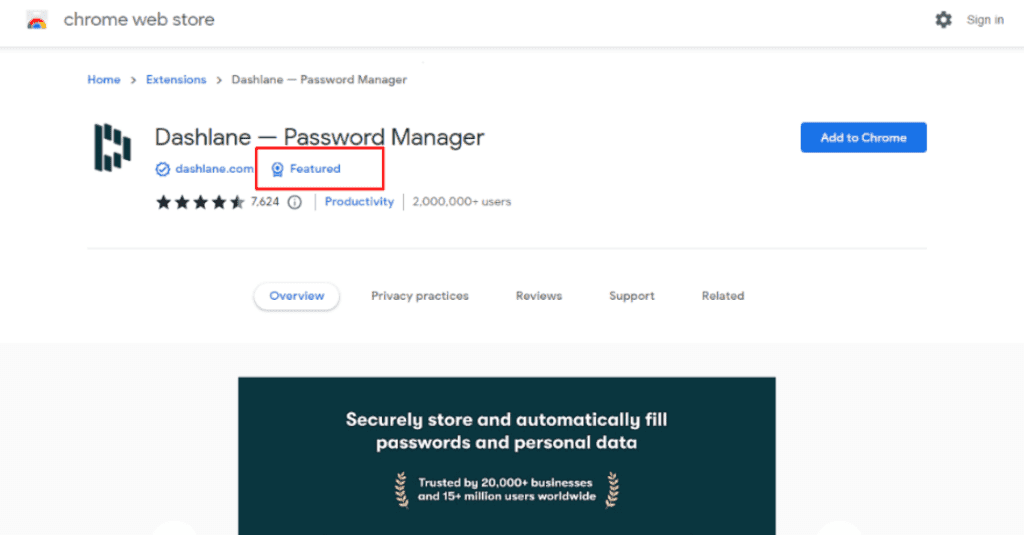
Follow the steps above to install the most credible browser extensions that will respect your digital privacy. The Chrome Web Store team also reviews extensions listed on its marketplace and provides the “Featured” badge for extensions that meet their CWS security standards. Try to stick to extensions with the “Featured” badge to make sure your chrome extensions are safe.
How to check your Google Chrome extensions
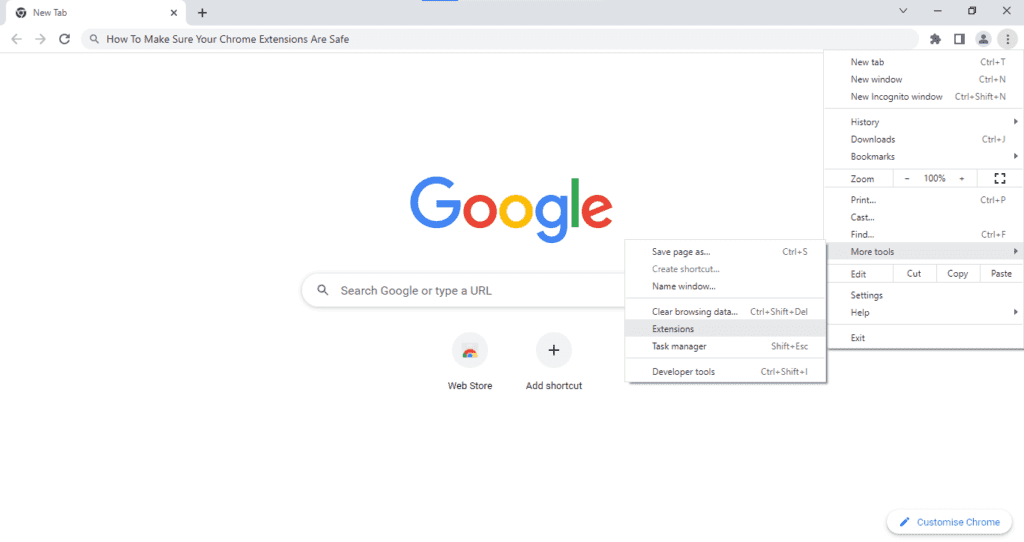
There are 3 ways to access your Chrome extensions. The first way is:
- Open the Google Chrome web browser.
- Select the 3-dot menu in the upper-right corner of the toolbar.
- Go to “More Tools.”
- Select “Extensions.”
The second way is:
- Open the Google Chrome web browser.
- Go to the Menu Bar.
- Select “Window.”
- Select “Extensions.”
The third way is:
- Open the Google Chrome web browser.
- Select the Extensions icon in the toolbar (it looks like a puzzle piece).
- Select the 3-dot menu to the right of the extension.
- Select “Manage extension.”
How to safely remove Google Chrome extensions
If you want to delete any Chrome extensions, follow these steps:
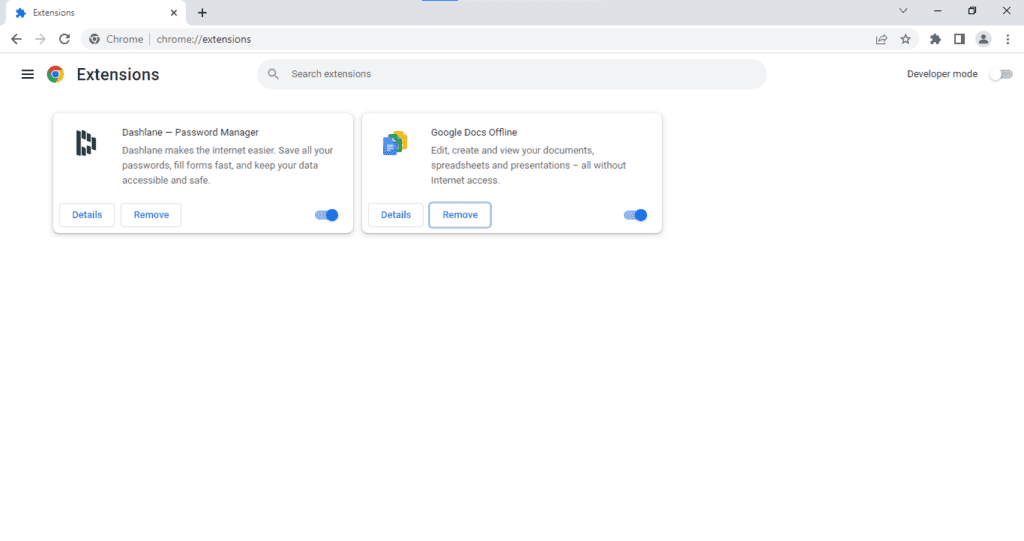
- Open the Google Chrome web browser.
- Select the 3-dot menu in the upper-right corner of the toolbar.
- Go to “More Tools.”
- Select ‘Extensions.’
- Select “Remove” on the extension you want to remove.
- Confirm by selecting “Remove” in the extension pop-up.
Your Google account is connected to your extensions, apps, linked accounts, and any websites you’ve visited. These conveniences are bound to expose your data to security risks online. Follow these 4 steps to secure your Google accounts today.
How to check your extensions on other browsers
There are extensions for all browsers, and here’s how to check them.
How to check Safari extensions
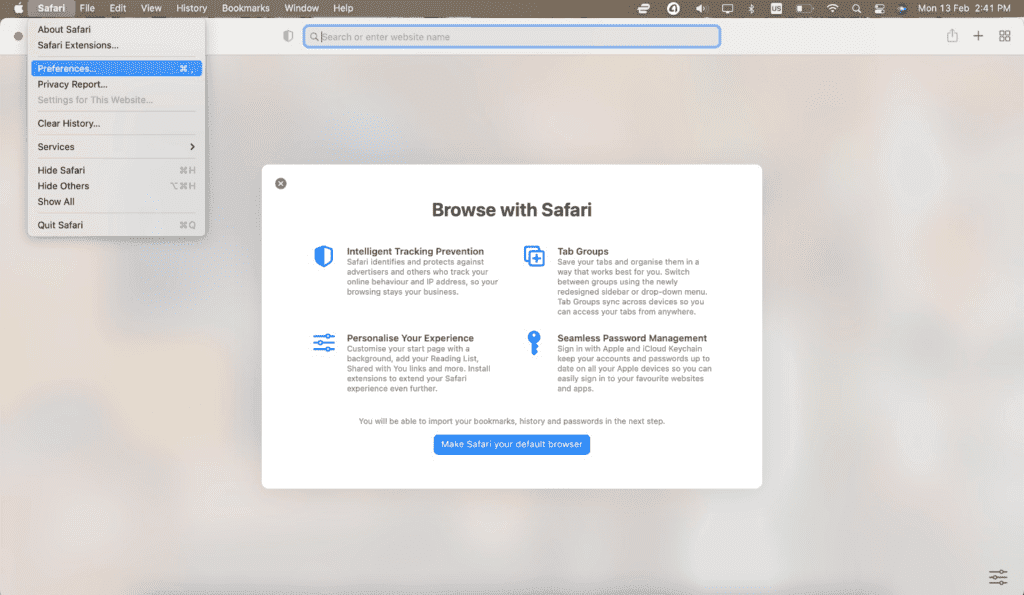
- Open the Safari web browser.
- Go to “Safari” in the menu bar.
- In the menu, select “Preferences.”
- Select “Extensions.”
How to check Microsoft Edge extensions
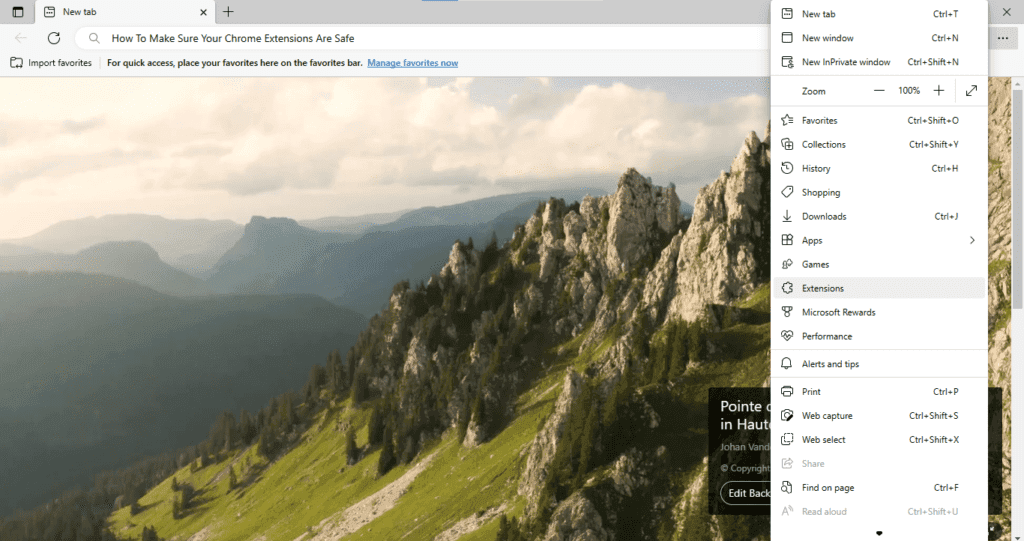
- Open the Microsoft Edge web browser.
- Select the 3-dot menu in the upper-right corner of the toolbar.
- Select “Extensions.”
How to check Firefox extensions

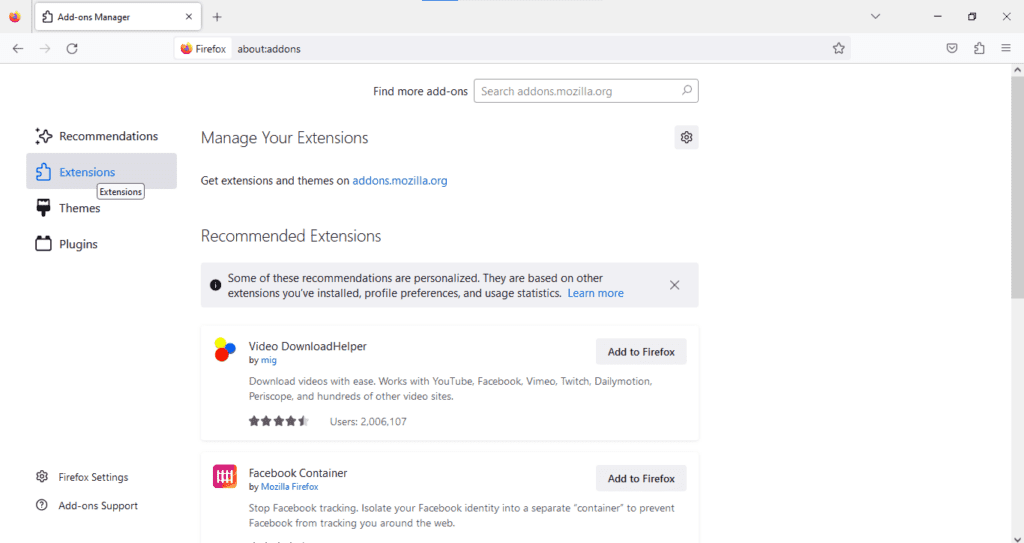
- Open the Mozilla Firefox web browser.
- Right-click the menu, shown as 3 horizontal lines in the upper-right corner of the toolbar.
- Select “Add-ons and themes.”
- Select “Extensions” on the left panel.
Is the Dashlane Chrome extension secure?
Yes! The Dashlane web extension is always secure and always private. The extension uses AES-256 encryption and Argon2 key derivation to scramble your data and turn your browser into a fortress. It also protects your data from phishing attacks and third-party corruption.
Dashlane takes special care in ensuring our browser extension security. We always sign and submit the extension to the store to prevent anyone from tampering with the code. In addition, the Dashlane extension uses a sandbox to secure your data from other websites and extensions.
To learn more about how Dashlane approaches browser extension security, take a closer look at how we continuously tackle attack scenarios and evaluate threats to keep your data secure.
Hybrid work comes with unique cybersecurity challenges like public WiFi, unsecure password sharing, and distractions at home (resulting in human error and phishing attacks). Download Dashlane's Guide to Hybrid Work to secure your workplace today.
References
- MakeUseOf, “6 Ways to Make Sure Your Chrome Extensions Are Safe,” March 2022.
- Alphr, “Can Chrome Extensions Be Dangerous? Yes, So Be Safe With These Tips,” September 2022.
- Berkley Information Security Office, “Browser Extensions: How to Vet and Install Safely”
- Chrome Web Store Help, “Permissions requested by apps and extensions”
- Dashlane, “Introducing Our Improved VPN Experience,” October 2021.
- Dashlane, “A Deep Dive into Web Extension Security,” August 2021.
- Dashlane, “Building for Security in a Browser Environment,” January 2021.
- Forbes, “Securing The New Hybrid Workplace And Keeping Your Employees Protected,” December 2021.
Sign up to receive news and updates about Dashlane
