Identity Theft Types & Prevention Strategies for Online Safety
Identity theft is a serious crime that can impact every aspect of your life, including your finances, career prospects, and reputation. That’s why it’s critical to take steps to protect your identity. The best way to begin is by learning more about the common identity theft types and comprehensive protection strategies.
What is identity theft?
Identity theft occurs when someone else uses your personal or financial information without your permission. Commonly stolen or intercepted information used to commit fraud or complete unauthorized transactions includes social security numbers, credit card numbers, banking information, names, and addresses. Identity theft is a crime that has become more common over the years as the internet leaves more personal data exposed.
Who is affected by identity theft?
Identity theft isn’t just something that happens to other people. Almost anyone can become the unsuspecting victim of an identity theft crime, often without realizing it. Those who can be affected by these crimes include:
- Individuals: Everyone should take steps to safeguard personal information like social security numbers, which cybercriminals and identity thieves often seek out. In the U.S., individuals between the ages of 30 and 39 reported the most identity theft cases per capita in 2023.
- Businesses: Identity thieves often target organizations to capture large amounts of employee and customer data, including names, addresses, and contact lists to sell on the dark web or use to support social engineering-based attacks on the business itself.
- Students: The younger generation is more internet savvy, but many students have higher levels of social media sharing, public WiFi usage, and other digital interactions that also leave them more vulnerable.
- Banks: Ready access to cash makes banks and other financial institutions common identity theft targets, with over 25% of banks in major economies reporting at least 100 identity-related incidents per year.
- Government agencies: Organizations including the IRS, ENISA, and state unemployment agencies remain vigilant against cybercriminals attempting to steal information from tax returns and other highly sensitive documents or impersonating others to collect their benefits and refunds.
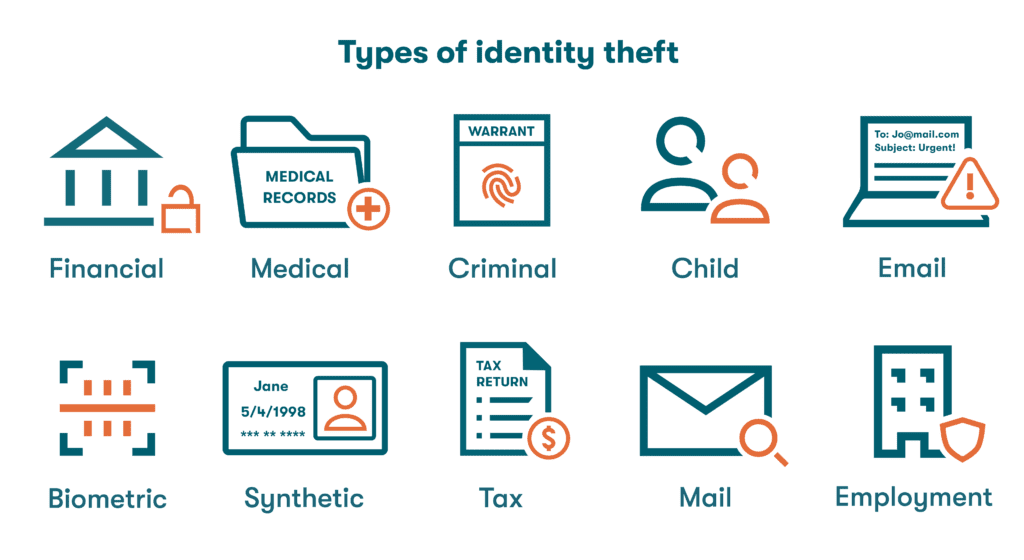
10 types of identity theft
Classic identity theft examples like stolen social security numbers and unauthorized new accounts funding big ticket purchases are certainly among the most common types of identity theft, but there are many other less obvious identity theft types that require vigilance.
- Financial: The primary motivation behind many identity theft cases is using the other person’s identity to obtain credit, duplicate debit cards, or gain access to bank accounts and drain funds. In 2023 alone, $43 billion was lost through financial identity fraud in the U.S., leading more individuals to consider identity theft insurance.
- Medical: Money is not the only thing that can be stolen during identity theft crimes. Personal information can also be used to obtain medical treatment or prescription drugs illegally. These activities can impact both the medical records and the reputations of the victims if left undetected.
- Criminal: A common motivation for assuming the identity of another is to avoid arrest warrants, fines, and other legal problems. This behavior detrimentally impacts the life and reputation of the other party by making them accountable for the criminal’s actions until they discover and resolve the issue.
- Child: Unfortunately, children are also targeted by identity thieves since they usually don’t have an established credit history and, therefore, aren’t monitoring their own credit regularly. Creditors don’t always verify the age of applicants. These factors can allow the fraud to go on undetected while creating surprise credit headaches for the child and their family members.
- Email: When a cybercriminal gains unauthorized access to someone's email account, they can steal private information from email messages, commit fraud, or impersonate the email owner—all of which can lead to significant financial and reputational consequences.
- Biometric: One of the newest forms of identity theft involves the forging of biometric information like voices and likenesses to deceive biometric-based authentication systems. The rise of artificial intelligence is providing better tools for scammers to pull off these emerging biometric identity crimes.
- Synthetic: By putting together stolen names, addresses, and social security numbers in a random fashion to create a fictitious individual, synthetic identity theft allows criminals to open accounts or access services under a completely fabricated identity. Without a targeted victim to report the crime, it’s difficult to detect and trace, and it can potentially impact multiple individuals simultaneously.
- Tax ID theft: Another common application for stolen social security numbers in the U.S. is the filing of false income tax returns. The scammer will file a return in the name of another individual, hoping to collect a refund before a legitimate return is filed and the scam is detected by the IRS.
- Mail ID theft: With so much emphasis placed on our digital footprint, it’s important to remember the trove of personal and financial information that can be found in the mail. Keeping mailboxes locked and shredding paper waste are effective ways to prevent mail theft and tampering.
- Employment theft: Employment-based identity theft occurs when someone uses another person's personal and background information to gain employment. This can result in serious consequences for the victim, including complications with their retirement benefits and taxes.
Use these strategies to avoid becoming an identity theft victim
Just as you protect your wallet, valuables, and private documents by ensuring no one gains access to them without your permission, you can protect your identity from hacking and scams by taking a few basic precautions.
- Don’t fall for phishing scams. The social engineering tactic known as phishing often uses emails that appear to be reputable to trick recipients into downloading malware or providing personal information like account numbers, credentials, or social security numbers. You can avoid phishing scams by staying on the lookout for telltale signs like poor grammar, excessively urgent requests, and URLs that don’t align with the real company website. However, phishing emails are only getting more sophisticated, so they won’t always have these obvious signs.
- Use a VPN on public WiFi. Public WiFi networks found in cafés, malls, and airports are vulnerable to hacking tactics like spoofing and man-in-the-middle attacks designed to intercept your sensitive information. When you join a public WiFi network, you should always use a virtual private network (VPN) to encrypt communication to and from your device.
- Use strong passwords. It’s best to make your passwords at least 12 characters long and include a random mix of uppercase letters, lowercase letters, numbers, and special characters. One of the best ways to ensure your credentials are consistently strong and secure is by using the password generator feature of a password manager.
- Don’t reuse passwords. We’re all naturally inclined to create credentials that are easy to remember, but the habit of reusing passwords diminishes identity protection and password security. Many accounts can be compromised if just one reused password is lost or stolen.
- Use multi-factor authentication. 2-factor authentication (2FA) uses a second credential, such as a push notification or code sent through an app or text, to confirm user identity. 2FA should always be enabled when available to neutralize many common hacks. With 2FA protection, cybercriminals who buy or steal your credentials also need to have access to your device or biometrics to gain unauthorized access.
- Protect your digital identity online. Your digital identity consists of all the information about you that exists online, including usernames, profiles, social media activity, digital interactions, and any other data that represents your online presence and behavior. You can protect your digital identity online by maintaining good password hygiene, using privacy settings whenever possible, and being cautious about the information you share.
- Use a password manager. A password manager helps you identify your weak passwords and replace them with strong, random, and unique passwords to better protect your identity. The best password managers raise your security profile by utilizing an encrypted vault for secure password storage and many also have convenient autofill features to eliminate the need for password memorization and unsecure storage.
What to do if you've been the victim of identity theft
Once you know (or even suspect) you have been a victim of identity theft, there are a few basic steps and precautions you can take right away to minimize the impact.
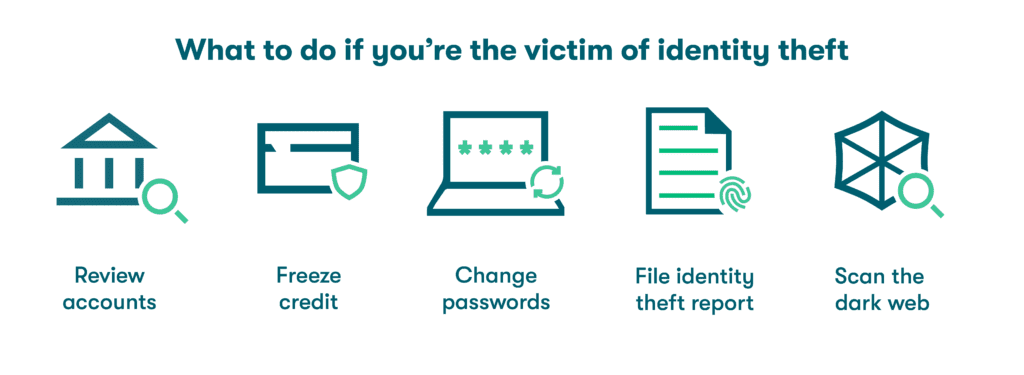
- Review banking and credit information. Scammers often start with smaller purchases to avoid notice, so you should carefully review all bank and credit card accounts to ensure there are no fraudulent charges. Contact your bank right away and alert them if you spot a potential issue.
- Freeze financial accounts. Placing a hold on active credit accounts is essential if you suspect fraud. You should also cast a wider net by contacting creditors and the major credit bureaus directly to report the theft, and freeze your credit history to minimize the impact on your credit scores.
- Change your passwords. Make it a priority to update passwords for compromised accounts to eliminate further activity. Use a password generator to easily replace existing credentials with strong and unique options. It’s also best practice to turn on multi-factor authentication for any accounts that offer it.
- File an identity theft report. Identity theft reporting creates a paper trail you can reference as you continue to rectify the situation with creditors and others that may have been impacted. In the U.S., you can visit www.identitytheft.gov to quickly file a report with the Federal Trade Commission (FTC).
- Check the dark web. A quick scan of the dark web is one of the easiest ways to find out if your personal information has already been compromised or exchanged by cybercriminals. Dashlane’s Dark Web Monitoring includes up to five email addresses and immediately alerts subscribers if their credentials are detected and need to be changed.
How Dashlane supports identity protection
Strong credentials are one of the best sources of identity protection in the digital age. Dashlane’s password manager improves both security and convenience while eliminating the need to create and remember strong credentials for each device or account. Additional features like VPN, 2-factor authentication, Dark Web Monitoring, and a secure sharing portal contribute to the comprehensive identity protection solution. Plus, an intuitive Password Health score allows you to continually monitor and improve your password hygiene.
As cyberattacks grow increasingly sophisticated, it becomes more important for individuals to stay vigilant to identify potential cyber threats and improve their security posture. To learn more about preventing and preparing for social engineering attacks, check out our webinar.
References
- USAGov, “Identity theft.”
- Thomson Reuters, “Identity theft is being fueled by AI & cyber-attacks,” May 2024.
- LifeLock, “Victims of identity theft: Who is targeted and why?” May 2024.
- Dashlane, “You Asked, A Hacker Answered: 7 Questions With Rachel Tobac,” October 2021.
- EMARKETER, “Identity fraud is costing banks big, and it’s burdening small banks the most,” April 2023.
- Attorney General of Washington, “AG Ferguson’s innovative unemployment fraud recovery initiative nets $42 million,” September 2023.
- AARP, “Identity Fraud Cost Americans $43 Billion in 2023,” April 2024.
- Office of Inspector General, “Medical Identity Theft.”
- Federal Trade Commission, “How To Protect Your Child From Identity Theft.”
- Dashlane, “What To Do If a Scammer Has Access To Your Email Address,” April 2023.
- Equifax, “What Is Synthetic Identity Theft?”
- Dashlane, “What Is a Digital Footprint and Why Is It Important?” August 2023.
- Troy, “Mail Theft in 2024: FinCEN Alerts Banks of Growing Crime,” March 2024.
- Dashlane, “Why Dashlane Will Never Ask You for Credentials in an Email (Because That’s How Phishing Works),” November 2021.
- Dashlane, “Identity and Access Management: Your Guide to Common Terms,” January 2023.
- Dashlane, “The State of Digital Identity,” December 2019.
- Equifax, “Fraud and active duty alerts.”
- USAGov, “How to place or lift a security freeze on your credit report.”
- Dashlane, “Dark Web Monitoring: Your Employees Are Likely Using Compromised Passwords,” July 2022.
Sign up to receive news and updates about Dashlane
