The Truth About Cybersecurity Awareness Month
Guest contributor Naya Moss is an international IT pro and infosec leader. She's dropping by with some truth about Cybersecurity Awareness Month and how you can take action all year round.
Don’t miss her free webinar on creating a human-centric security culture!
The truth about Cybersecurity Awareness Month is...we need to be cyber aware all year long! As consumers, professionals, employees, parents, and family members, we all should have a continuous approach to cybersecurity. Security professionals want you to be continuously aware of your security posture and have a security threat model in your work and personal lives.
Over the past decade, we have seen cyberattacks and crime cross over into the lives of everyday citizens such as the Colonial Pipeline cyberattack. We have seen businesses and folks of all backgrounds become victims of breaches, leaks, ransomware, and more. In 2021, we have seen many cyberattacks. It almost feels normal, no longer a shock. This is the exact reason why we should take Cybersecurity Awareness Month activities beyond the month, make continuous efforts, and make security normal—a part of our everyday lives.
Tips for your work life
Get to know the IT, Security, HR, and Operations Departments
Particularly in the remote workforce, there is a rise in social engineering attacks. You are less likely to know the org chart in your company and who works in which department. Hackers know that remote workers are vulnerable to scams and accidentally leaking information. If you ever receive a phone call from someone claiming to be from your IT department, you should verify first that they work at your company and that you are speaking with the person they claim to be. Perhaps offer to do a video call to verify their identity.
Be honest about your knowledge level
When starting a new job, you may be onboarded to all sorts of new tools, technology, and software. Suppose you have previously worked in a startup and have moved on to a more corporate environment or the education sector. In this scenario, you may come across stricter policies and procedures.
During your first few weeks, you might receive an onboarding from IT or security that was perhaps rather quick, and you might feel like there were things you did not understand, and you would like to know more. Take some time to research and reach out to the IT and or Security team and ask them for help. Security professionals are excited and explain that you want to know more to better yourself and the company, security-wise.
Inform your company when traveling
Suppose you are traveling for work or vacation and thinking about bringing your work laptop. Inform the IT and Security teams; it's imperative for them to be aware of your travels and any potential suspicious activities. Some companies may provide VPN software to keep you safe and protect your data while working or browsing public Wi-Fi. In the unfortunate case that your laptop gets lost, stolen, or broken while exploring the wonders of the world, your IT and Security team will be aware and prepared to respond quickly.
Tips for home and personal
Gradually incorporate cybersecurity learning into your daily life. Create your security checklist. Here is a baseline example list to get started:
Marie Kondo your general digital presence & improve your security posture
Many of us sign up for dozens of new software services and regularly install extensions and integrations every year. Rather than taking several hours at once, schedule small time blocks of 10-15 minutes a week to clean up your digital presence. Here are a few example items:
- Write a list of all known accounts and enable two-factor/multi-factor authentication, typically within a software service’s security and privacy settings.
- Protect your sensitive personal identifiable information (PII). Regularly remove your personal information from the internet by emailing providers directly or using a service such as Delete Me and Deseat Me.
- Upon news of a recent breach or leak, check if your email was included using a website like Have I Been Pwned. If you are using Dashlane, check out How to set up and use Dark Web Monitoring.
- Protect your identity against fraud; take preventative measures by freezing your credit.
- Every quarter, search yourself using Google search in an incognito browser window. Find out what information about you others can see and find on the internet. You might be surprised to see your address, phone number, family members, and more!
Phone
- Enable screen lock.
- Install software updates regularly.
- Call your carrier and request instructions on how to set up a carrier security pin.
- Check app permissions. Turn off services such as location, microphone, and photos access where no longer necessary.
Laptop
- Regularly use a password manager (laptop and phone).
- Encrypt your hard drive.
- Regularly install updates.
- Set to lock after 15 minutes.
- Install and migrate to security- and privacy-focused browsers such as Brave, Firefox, or Safari.
- Invest in hardware-based authentication via a FIDO Security Key such as Yubico.
Home & hardware
- Secure your home's wireless network. Change the default SSID and administrator password on your home router and wireless access point.
Social media
Other tips to consider (based on your threat model)
- Instead of a password, use a phrase or sentence made of a few words, known as a passphrase. It's different from a password, which is typically one word or string of letters, characters, and numbers.
- Limit social media-based logins like Login With Facebook. Don't put all your eggs in one basket. The day Facebook went down for 6 hours, many were unable to log in to accounts or services using Facebook’s social login.
Incorporate security news into your daily or weekly routine
- Podcast enthusiast? You will love WIRED Security: News, Advice, and More.
- On the more advanced side of the tech, you'll love This Week In Security.
- For leaders, executives, and stakeholders in organizations, Last Week As A vCISO is the right newsletter for you.
Cybersecurity entertainment
Swap 1 hour a month on Netflix or TV to listen to deep dives into real-life cybersecurity stories and crimes. Learn from ethical hackers (people who hack for good) and perpetrators themselves how attacks are planned, executed and how everyday exploits work. Here are some great listens below:
- Darknet Diaries
- Hackable? by McAfee
- Hacking Humans
- Malicious Life by Cybereason
Where to get started for Cybersecurity Awareness Month
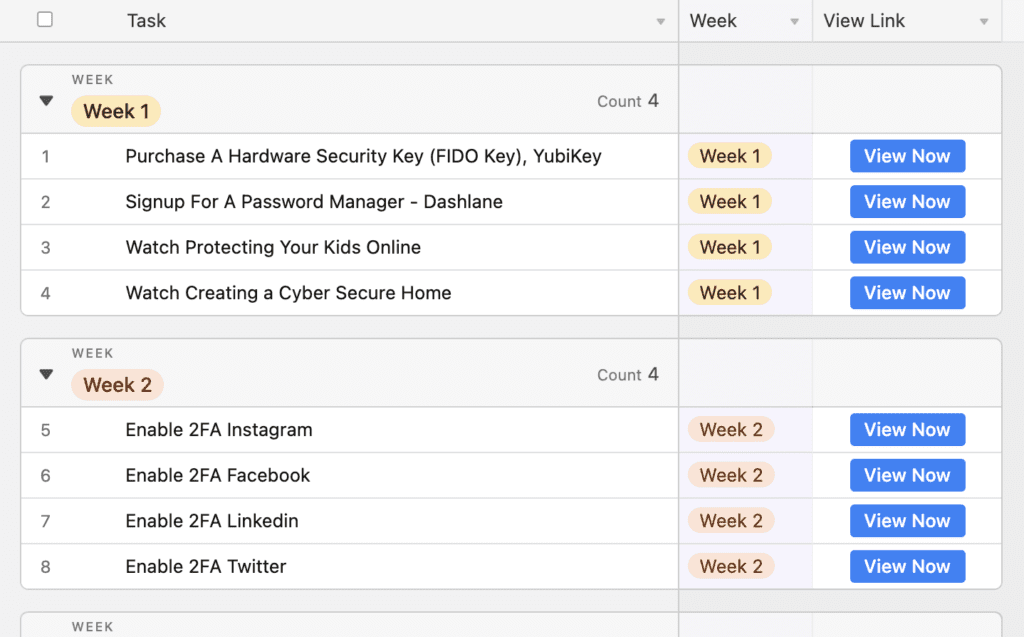
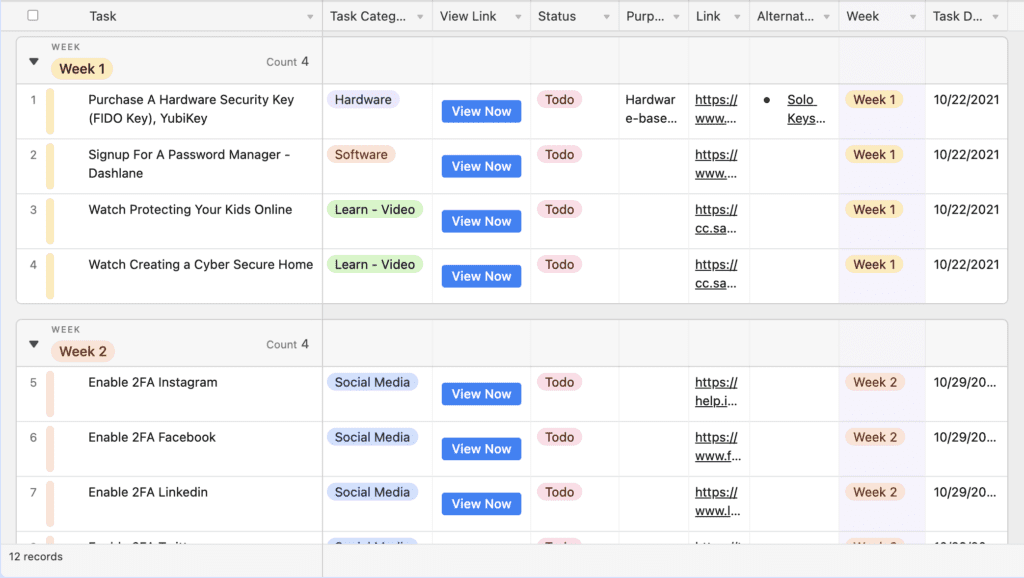
If you have found this list helpful, we have two example Personal Security Posture Improvement Plans for you below:
Beyond Cybersecurity Awareness Month
Most important of all, take time to learn about hacks, breaches, and leaks. Informing ourselves of cyber events and crimes helps us to build our understanding of cybersecurity and helps us so that we can protect ourselves and our families better.
Learning about cybersecurity and incorporating building a good security posture into your life can feel overwhelming. Nevertheless, when done in increments and continuously throughout the year, you'll get it done!
Sign up to receive news and updates about Dashlane