What Is Credential Stuffing and How Can It Impact You?
Credential stuffing is a dangerous hacking tactic that takes advantage of stolen account credentials and rapidly growing automation to systematically commit cybercrimes. Recent news reports warn us of the danger of these attacks, but heightened awareness and some informed best practices can lessen their impact. What is credential stuffing, and what tools are available to prevent and detect credential stuffing attacks?
What is credential stuffing?
Credential stuffing is a common hacking tactic that uses large sets of stolen usernames and passwords paired with automated software tools to gain unauthorized account access. Hackers methodically input combinations hoping to obtain a match with one or more user accounts, and reused passwords multiply their odds of success. If you’ve ever forgotten your password and then tried plugging in other credentials hoping to guess correctly, then you understand the basic credential stuffing definition.
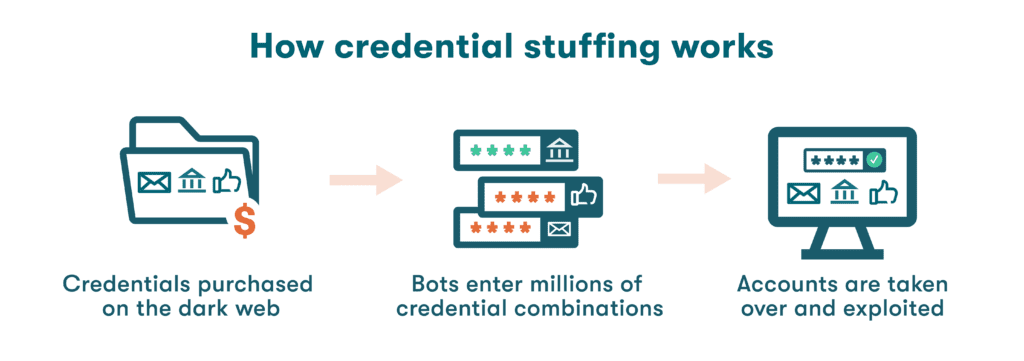
How credential stuffing works
What is a credential stuffing attack? Credential stuffing is carried out based on a highly organized and consistent set of actions that can eventually lead to a data breach, corporate espionage, or identity theft.
- It starts with stolen passwords: Despite the stereotype of the lone hacker, a credential stuffing attack is not typically carried out by the same person or group who originally stole the usernames and passwords. Instead, an underground industry has evolved for the sale and purchase of credentials on the dark web. The market value of these stolen credentials varies, with online retail and financial accounts considered quite valuable.
- Bots are used to enter credentials: The term bot is used to describe an automated software application used to perform repetitive tasks. During a credential stuffing attack, these tools can input millions of credential combinations in a short period of time. A botnet takes this approach a step further when malicious bots on multiple network-connected devices work together.
- Accounts are taken over and exploited: Less than 4% of credential stuffing attacks are successful, but this has not deterred cybercriminals. When they do find a match, damage can be inflicted in multiple ways, including unauthorized financial transactions and identity theft. For businesses, a credential compromise might lead to regulatory violations, including the California Consumer Privacy Act (CCPA) and the General Data Protection Regulation (GDPR), if customer data is included in the breach.
Want to learn more about using Dashlane Password Manager at home or at work?
Check out our personal password manager plans or get started with a free business trial.
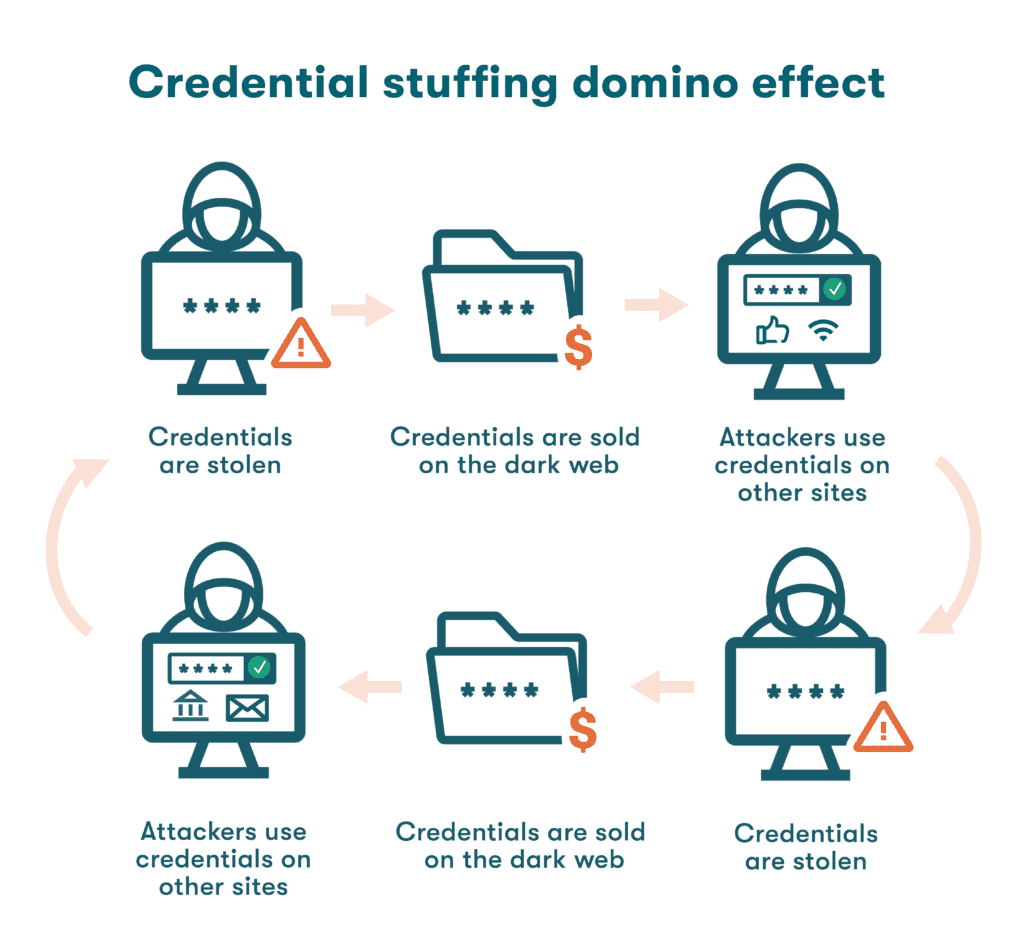
The credential stuffing domino effect
When a cybercriminal finds a match between stolen credentials and user accounts, they don’t stop there. Hackers are well aware that over 50% of passwords are reused. When stolen credentials can be used to unlock many accounts, it creates a domino effect that heightens the size and severity of a single data breach.
Examples of recent credential stuffing attacks
Recent news provides many examples of credential stuffing attacks impacting well-known companies. These attacks are evidence of credential stuffing tools capable of evading many conventional cybersecurity practices:
- Norton LifeLock: In January of 2023, Gen Digital, the parent company of Norton LifeLock, notified 6,500 password manager customers that their names, addresses, and phone numbers might have been exposed as the result of a credential stuffing attack. Since the stolen credentials also provided access to private password vaults, Gen Digital informed customers that saved passwords within the Norton password manager may have been accessed.
- PayPal: Digital payment leader PayPal was the subject of a credential stuffing attack in December of 2022 that impacted approximately 35,000 users. The credentials in question were believed to be reused by customers for PayPal accounts before they were stolen in some other data breach. Although no unauthorized financial transactions were reported, users' social security numbers, birth dates, and addresses were exposed.
- The North Face: Outdoor apparel company The North Face was impacted by a large-scale credential stuffing attack involving over 194,000 customer accounts between July and August of 2022. Customer information including names, addresses, and telephone numbers were exposed, but no customer credit card information was stored on the website. Unlike many recent password attacks, it wasn’t known whether the credentials had been stolen during an unrelated breach and resold on the dark web or were stolen directly from The North Face website.
- Zola: The popular wedding planning site Zola saw 1% of its customers impacted by credential stuffing in May of 2022. In a particularly unsavory twist, gift cards and money were stolen from newlyweds or soon-to-be newlyweds, while their email accounts were changed to deny them access. Zola reacted to these crimes immediately to protect customers and replace stolen funds.
- General Motors: In April of 2022, car manufacturer General Motors (GM) experienced a credential stuffing attack during which the reward points of many customers were redeemed without proper authorization. Once again, the credentials were believed to be obtained from a previous data breach of a non-GM organization. GM advised all impacted customers to reset their passwords and check their financial statements immediately.
It’s easy to begin enjoying Dashlane’s best-in-class user experience, security features, and customer support, even if you’re already using another password manager. Our simple step-by-step instructions explain how to switch your password manager to Dashlane today.
How to detect credential stuffing attacks
Credential stuffing has some telltale signs that can be detected early when you’re armed with advanced monitoring tools. Signals to keep an eye out for include:
- Repeated login attempts. One way to prevent credential stuffing is by monitoring traffic for unusual login patterns. Automated attacks might be given away by an unusually high number of login attempts from multiple geographic locations or other behavior patterns associated with machine learning algorithms.
- High login failure rates. Repetition and persistence are the keys to credential stuffing. Limiting the number of unsuccessful login attempts is a good way to separate human error and forgetfulness from malicious intent. NIST standards recommend lockout policies to limit the number of unsuccessful credential guesses.
- Malicious IP addresses. Another important clue left behind during credential stuffing attacks is the Internet Protocol (IP) addresses from which the hacks originated. Blacklisting practices can be used to block suspicious IP addresses known to be involved in previous breach attempts. Even when IP addresses are continually cycled to elude detection, improved threat intelligence allows cybersecurity teams to adapt to these changes quickly.
- Dark web monitoring. In some instances, stolen passwords and personal information identified through dark web monitoring might be found a little too late. However, since passwords are often exchanged on the dark web before they’re used for credential stuffing, monitoring the dark web to determine your exposure level is an important part of credential stuffing prevention.
How to prevent credential stuffing attacks
Credential stuffing and password security are closely linked, so the tools and practices you use to improve your password hygiene are essential, along with a few other best practices.
- Don’t reuse passwords. Repeating old credentials is a common habit since we all want to make our passwords easier to remember. Unfortunately, reusing passwords also decreases password security, because multiple accounts can be breached if a reused password is compromised. Password reuse makes us much more vulnerable to credential stuffing attacks by increasing the chances of a successful match.
- Keep software updated. Software and operating system updates also include patches to correct any known security issues. Hackers take advantage of unpatched software and out-of-date operating systems to gain unauthorized access. A cybercriminal might even scour the internet to find unpatched systems to target. Applying recommended patches and updates helps prevent the data breaches that credential stuffers rely on.
- Use 2-factor or multifactor authentication. Push notifications and codes sent through an app or text to verify user identity are common examples of 2-factor authentication. This security practice is extremely effective in preventing successful credential stuffing attacks because the hacker is unlikely to have access to the second credential. Multifactor authentication (MFA) uses two or more identifiers for the same purpose, sometimes including biometric factors like fingerprints or facial recognition.
- CAPTCHA. Credential stuffing attacks are one reason we’re often asked to prove we’re human by solving a puzzle or identifying objects in a grid before accessing a website, using what is called a Completely Automated Public Turing test to tell Computers and Humans Apart (CAPTCHA). Although they can become an annoyance, CAPTCHAs effectively block automated software from gaining full access independently.
- Only share passwords securely. Sharing passwords with friends, family, and coworkers is almost unavoidable, especially for services like video streaming and company social media accounts. Password sharing increases vulnerability to password theft when an unencrypted method like a text or Slack message is used for sharing. In addition, sharing passwords exposes everyone in the group if any one of them is impacted by a cybercrime.
The best way to share passwords securely is by using the sharing feature of a password manager. Dashlane’s password sharing tool can be used to safely share credentials or Secure Notes with other Dashlane users. - For businesses, educate your employees. Employees should be trained to understand the connections between password hygiene and credential stuffing as part of an overall cybersecurity education program. Bring your own device (BYOD) and remote working policies also increase the risk factors for lost or stolen passwords, so all employees should be trained to remain vigilant and report security incidents quickly.
- Use a password manager. A password manager is an important tool for minimizing the impact of credential stuffing and password attacks. The best password managers raise your security profile by creating strong and unique passwords for each account, then storing them in a secure, encrypted vault. This helps to protect you from hackers who steal or guess at passwords to gain system access.
- Dark web monitoring. Despite being vigilant, you may not always realize when your information has been compromised. Dark web monitoring helps you scan the hidden recesses of the internet for your personal information and credentials. Dashlane’s Dark Web Monitoring includes up to five email addresses and immediately alerts subscribers if their credentials are detected and need to be changed.
- Consider passwordless authentication. 81% of hacking-related breaches leverage weak or stolen passwords to gain unauthorized access. Passwordless authentication including passkeys and biometric methods have the potential to eliminate long-standing hacking methods such as brute-force attacks and credential stuffing that exploit traditional password weaknesses.
Credential stuffing vs. other cyberattacks
Cybercriminals remain steadfast in their dedication to credential stuffing, despite the relatively low success rate. What separates credential stuffing from other cyberattack methods including phishing, zero-day attacks, ransomware, and man-in-the middle attacks is the undeniable connection between password security and an unsuccessful hack.
Dashlane uses advanced algorithms and encryption to generate, store, and autofill passwords safely. 2-factor authentication (2FA), Dark Web Monitoring, and a Password Health score to track your weak, reused, and compromised passwords provide additional layers of protection.

Hackers are real, and so is the need for hacker protection. To help you secure your online accounts and reduce your vulnerability to cyberattacks, check out these 8 hacker protection tips to keep your online accounts safe.
References
- Dashlane, “What Is Credential Stuffing?” December 2020.
- Dashlane, “6 Things a Safe Username Should Always Do,” February 2023.
- Dashlane, “The Dark Web Iceberg Explained In Simple Terms,” June 2023
- Amazon, “What is a bot?” 2023.
- HYPR Encyclopedia, “Credential Stuffing,” 2023.
- Investopedia, “General Data Protection Regulation (GDPR) Definition and Meaning,” November 2020.
- Dashlane, “A look at Password Health Scores around the world in 2022,” 2022.
- CPO Magazine, “Credential Stuffing Attack Impacts About 35,000 PayPal Accounts, Company Says No Unauthorized Transactions Detected,” January 2023.
- Dashlane, “Always Change Your Passwords After a Breach,” March 2020.
- The Hacker News, “What the Zola Hack Can Teach Us About Password Security,” August 2022.
- Dashlane, “The Most Notable Breaches That Kicked Off 2023,” April 2023.
- CPO Magazine, “The North Face Credential Stuffing Attack Compromises 200,000 Accounts,” September 2022.
- Infosecurity Magazine, “US Car Giant General Motors Hit by Cyber-Attack Exposing Car Owners' Personal Info,” May 2022.
- TechTarget, “Manage unsuccessful login attempts with account lockout policy," September 2020.
- Auth0, “Protect Your Site from Bots with CAPTCHAs and JavaScript Challenges,” February 2023.
- Dashlane, “Dark Web Monitoring: Your Employees Are Likely Using Compromised Passwords,” July 2022.
- Dashlane, “Digital Identity 101: Everything You Need to Know,” April 2023.
- Dashlane, “7 Password Hygiene Best Practices to Follow,” February 2023.
- Dashlane, “How Password Reuse Leads to Cybersecurity Vulnerabilities,” May 2023.
- Dashlane, “What Is Password Sharing & When Should I Use It,” February 2023.
- Dashlane, “Share your saved items in Dashlane,” 2023.
- Dashlane, “3 Strategies to Prevent Breaches and Hacks at Work,” September 2021.
- Dashlane, “A Guide to Protecting Passwords from Hackers,” February 2023.
- Dashlane, “How a Password Manager Helps Prevent a Data Breach,” December 2017.
- Dashlane, “What the Hack is a Brute Force Attack?” February 2020.
- Dashlane, “Dark Web Monitoring,” 2023.
- Dashlane, “6 Pros & Cons of a Future Without Passwords,” July 2023.
- Dashlane, “2-factor authentication (2FA) in Dashlane,” 2023.
- Dashlane, “A look at Password Health Scores around the world in 2022,” 2022.
- Dashlane, “8 Hacker Protection Tips To Keep Your Online Accounts Safe,” May 2023.
- Dashlane, “How to Switch Your Password Manager to Dashlane,” January 2023.
Sign up to receive news and updates about Dashlane
