7 Password Hygiene Best Practices to Follow
With so many passwords and accounts needed to maintain our daily routines, it can seem overwhelming to manage passwords securely to protect our data and devices from cybercriminals, leading to password fatigue and shortcuts. Password hygiene is a concept that distills safe password management into a set of logical and easy-to-follow password security best practices.
What is password hygiene?
Password hygiene practices apply a set of principles to manage password habits, identify vulnerabilities, and make sustainable improvements to your security profile. These principles include:
- Selecting, managing, and maintaining strong passwords
Creating strong passwords is the first step on the path to password hygiene. Some of the essential requirements include using a mixture of uppercase letters, lowercase letters, numbers, and special characters in random order, avoiding common phrases and personal identifiers (such as your name and address) in your password, and using at least 12 characters.
Once strong passwords are in place, password best practices like encryption and 2-factor authentication help you continue the journey to improved password hygiene.
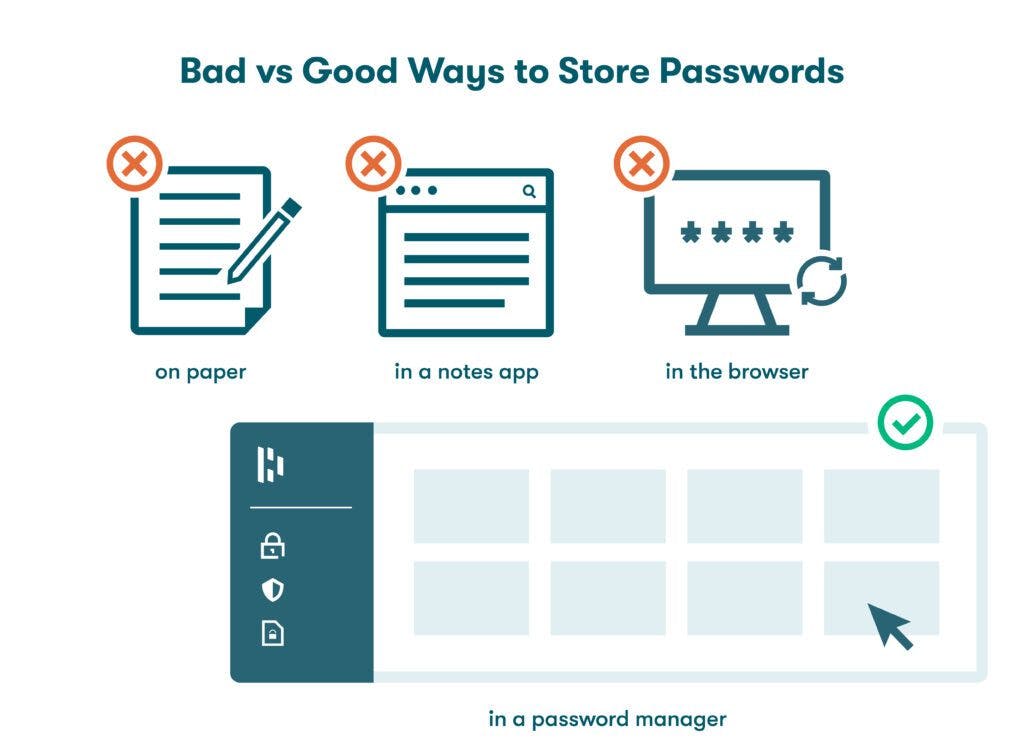
- Storing passwords securely
Safe password storage is the second pillar of password security, and this certainly doesn’t mean storage in drawers, spreadsheets, or browsers. To protect your passwords, you need to be sure that no one else can ever access them. The best way to store passwords safely is by using a password manager to create and store strong, encrypted passwords on secure external servers where they are protected.
- Keeping passwords private
Strong and safely stored passwords must also be kept private at all times. This means limiting password sharing with friends and family (and using a password manager to securely share passwords when absolutely necessary) and not forwarding passwords to others using email or text messaging. Proactive cybersecurity basics, including dark web monitoring, can verify that your efforts to maintain privacy are successful.
- Paying attention to overall password health
Password health is closely linked to password hygiene and is defined by the number of weak, reused, or compromised passwords a person has stored. If you have a password manager, you should have access to a password health score. Regularly reviewing your score helps you identify what passwords to change to improve password health. For businesses, collectively working to improve password health is a great way to build a strong security culture.
7 best password hygiene practices to follow
Once you understand the basics of password hygiene, you can learn how to protect passwords and other sensitive information consistently by applying a few password security best practices:
- Create strong passwords: Strong passwords that are as random and unpredictable as possible are much less vulnerable to hacks and data breaches. Tools like password managers make it easy to generate random, unpredictable passwords for all your accounts, then encrypt and store them safely. With a password manager, passwords are safely autofilled, so you no longer need to memorize them or write them down.
- Don’t reuse passwords: The high volume of new accounts we need to manage can make reusing passwords an easy habit to fall into, undermining password hygiene. Duplicate passwords weaken security by exposing multiple accounts if even one password is compromised. A password manager’s password health score identifies your reused passwords so that you can update them.
- Use multifactor authentication: 2-factor authentication (2FA) uses a second credential, such as a code sent through an app, to confirm your identity. This password best practice adds a few seconds to your login time but makes it much harder for a cybercriminal to access your accounts without having your device in their possession. Multifactor authentication (MFA) uses two or more factors for an even higher level of security. This can include biometric identifiers like fingerprints and facial recognition.

- Use a VPN on public WiFi: Many of us regularly use public WiFi in cafés, airports, and hotels. Unfortunately, these public WiFi networks can expose data traffic to interceptors, making them a target of choice for hackers. A VPN mitigates this risk by encrypting all data going into or out of the device and routing it through a secure portal. A VPN also masks your IP address, allowing you to browse the internet privately.
- Don’t share passwords insecurely: Sharing passwords with friends and family for WiFi networks, subscription services, and retail accounts is nearly unavoidable. This habit also makes you more vulnerable if anyone using your password(s) is impacted by cybercrime. Good password hygiene includes taking steps to share passwords safely using a password manager and avoiding paper notes, texts, or even communication platforms like Slack, where unencrypted messages can be stored indefinitely.
- Use a password manager: A password manager is one of the best ways to incorporate password security best practices and password hygiene into your daily online routine. By utilizing automated password generation, storage, and autofill features, you no longer need to manually create and remember complex passwords for each of your accounts—eliminating password fatigue. A password manager also helps you monitor your password health and organize passwords to improve productivity.
- Change your passwords only when necessary: How often should you change passwords? While there are no set rules, the digital identity guidelines published by the NIST explain that minor changes made during forced reset intervals have little value since hackers can use these predictable transformations to their advantage. This recognition, along with improved tools and technology like password managers, VPN, and 2FA, is making periodic resets like 30/60/90-day intervals obsolete. A safer and more logical approach to password resets calls for changing passwords only when:
—You know or think you’ve been hacked
—You discover malware
—You find your information on the dark web
—You use public WiFi without a VPN
—You share passwords insecurely

The risks of poor password security
Why do you need to worry about password health and hygiene? As the number of passwords, accounts, and devices the average person uses has grown, so has the frequency of cyberattacks and hacking attempts. Poor password hygiene can also complicate your daily routine as you pause to hunt for or recover lost credentials. There are four key risks that good password hygiene can drastically reduce:
- Forgotten or lost passwords
When passwords are not stored in an organized way, password management becomes less efficient and secure. If you lose passwords stored in notebooks or on slips of paper, you should immediately reset them to avoid compromising your credentials. Both computer users and IT teams can become frustrated with ongoing forget/reset loops when passwords are continually forgotten or lost.

- Brute-force attacks
A brute-force attack plugs in random combinations of computer-generated passwords and usernames until a match is found. Automation and artificial intelligence are making it easier for cybercriminals to cycle through these combinations quickly. Weak passwords are easier for cybercriminals to guess using a brute-force algorithm, so improving your password hygiene minimizes this type of threat.
- Credential stuffing
The hacking tactic known as credential stuffing takes lists of usernames and passwords stolen during a breach and attempts to use them to gain access to other accounts that can be exploited, such as bank accounts. The attackers rely on a small fraction of customers reusing credentials for multiple accounts so they can use the stolen information to access unrelated (and more valuable) accounts.
- Data breaches
Data breaches are security incidents that result in the disclosure of sensitive information like login credentials, account information, and intellectual property (IP). While hacking tactics are the methods used to gain unauthorized access to devices or servers, data breaches can be the costly result. These incidents are the most critical consequence of poor password security.
Among hard-to-use, narrowly focused security tools, Dashlane stands out as the universally loved, comprehensive credential manager that proactively protects admins, employees, and individual users with minimal effort.
Dashlane password manager makes it easy to improve your password hygiene, password health, and productivity all at once. Intuitive password creation features and a secure, protected vault help eliminate habits like password reuse and frequent password changes that can open the door to cyberattacks. A VPN adds a layer of security and convenience in public settings, while dark web monitoring ensures your credentials and identity always remain private.
For organizations, features like Credential Risk Detection, Dashlane Nudges, phishing alerts, and more with enterprise-grade security.
We analyzed password hygiene with anonymized data from millions of users and over 23,000 businesses protected by Dashlane to determine the state of password health in 2024. Find out the average Password Health score by region, the areas with the highest percentage of reused passwords, and more.
References
- Dashlane, “9 Practical Password Security Best Practices,” March 2023.
- Dashlane, “How Strong Is Your Password & Should You Change It?” August 2022.
- Dashlane, “The Risks of Using a Browser Password Manager,” October 2024.
- Dashlane, “Best Way to Store Passwords at Home or Work,” September 2022.
- Dashlane, “Stay Secure by Avoiding 7 Common Password Sharing Mistakes,” August 2023.
- Dashlane, “Do You Have These 6 Cybersecurity Basics Down?,” June 2022.
- Dashlane, “How to Shine a Light on the Dark Web,” June 2022.
- Dashlane, “How the C-Suite Can Lead Security Culture” March 2024.
- Dashlane, “Password Generator,” September 2022.
- Dashlane, “A Complete Guide to Multifactor Authentication,” November 2022.
- Dashlane, “Why Do You Need a VPN? Don’t Miss These 3 Key Benefits,” December 2022.
- NIST, “Digital Identity Guidelines,” 2023.
- Statista, “Annual number of data compromises and individuals impacted in the United States from 2005 to first half 2022,” 2022.
- Dashlane, “What the Hack is a Brute Force Attack?,” February 2020.
- Dashlane, “What Is Credential Stuffing and How Can It Impact You?,” November 2023.
- Dashlane, “How To Prevent and Respond to Data Breaches,” July 2023.
- Dashlane, “A Global Look at Password Health Scores in 2024,” 2024.
Sign up to receive news and updates about Dashlane
