Most Recent Posts
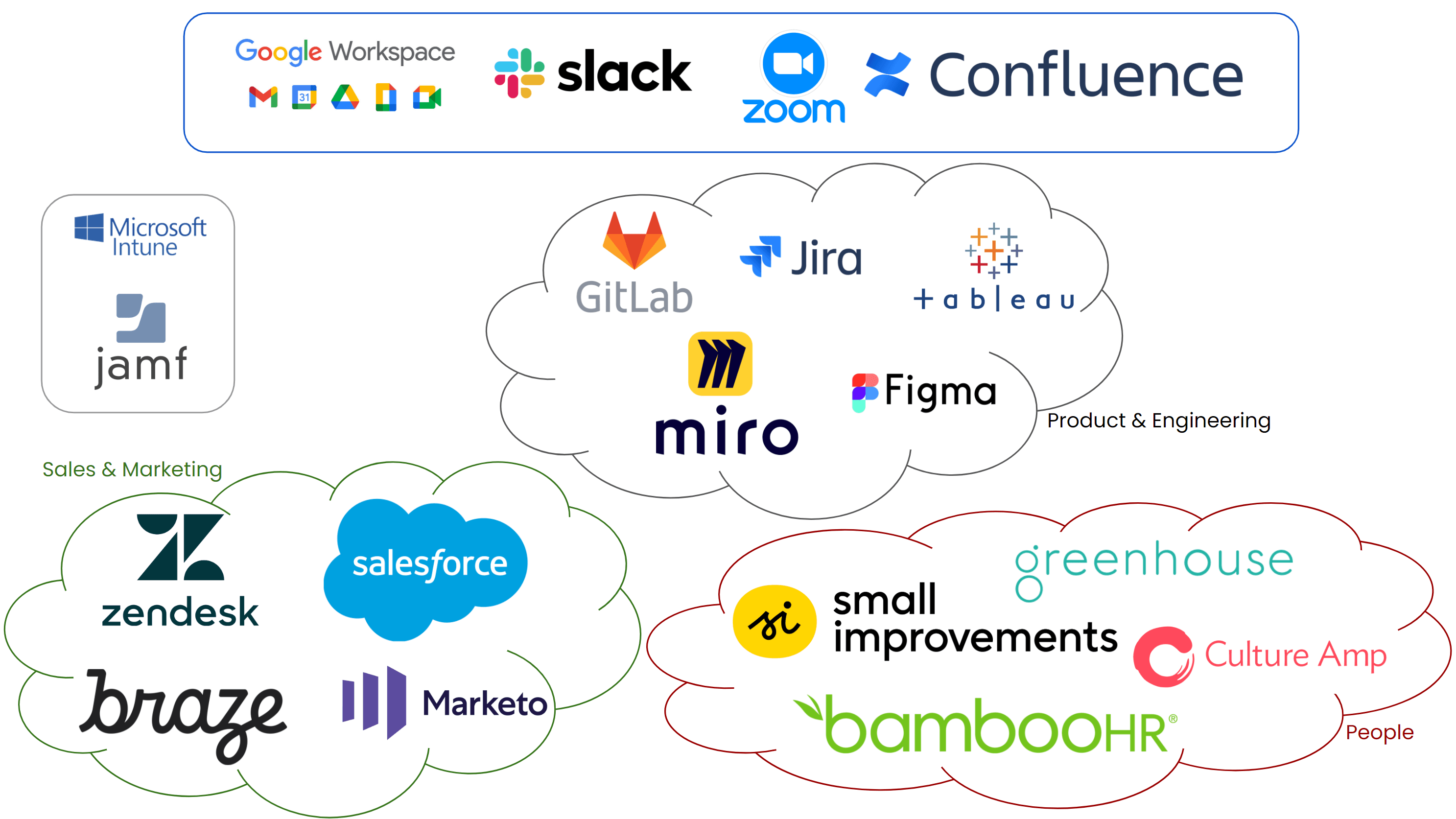
How We Do IT at Dashlane
We sometimes get asked by our business customers how we manage our internal IT to support our employees both efficiently and securely. In this article, I would like to open the curtain by sharing some of our IT practices and explaining how they correlate to efficiency and security. But let’s start with a bit of […]
2-Factor Authentication 101: What It Is and Why It Matters
2-factor authentication (2FA) adds a second layer of safety to your online accounts, but what exactly is 2FA, and why should you care?

U.S. Congress Steps Up Focus on Cybersecurity—and Individuals Should, Too
While the government tries to protect businesses from cyber threats with two new policies, you also need to take basic steps to protect yourself.

Real-World Examples of Data Breaches and Hacks in Colleges and Universities
Here are real-world examples of hacks and breached that happened to colleges and universities and how other institutions can prevent them.
A Guide to Password Managers for Colleges and Universities
Here’s a guide to how colleges and universities can use a password manager to take control of their cybersecurity.
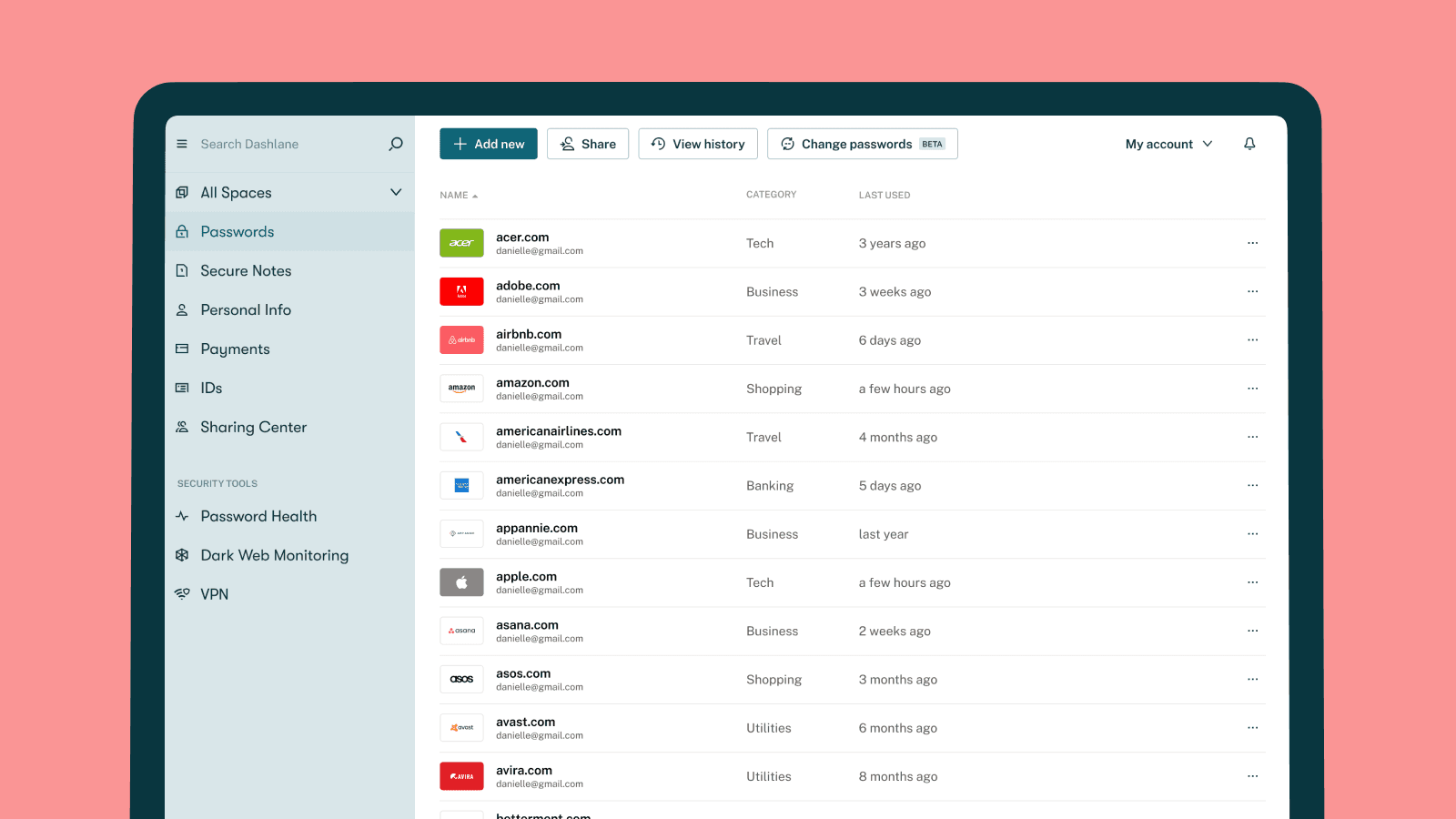
Product Updates: Two New Features You’ve Been Asking For
Dashlane now offers two highly requested new features: Secure File Storage and the ability to protect items with your Master Password.

The Benefits of a Dashlane Business or Omnix Trial
Here’s the business case for trying Dashlane before you purchase it for the whole team and how it can help create a culture of security.

Why Colleges and Universities Need a Password Manager
Here’s why every college and university needs to protect themselves with a password manager.

How a Small Architecture Firm Spotted Compromised Passwords and Secured Data
How Jeffrey Demure + Associates spotted their compromised passwords and secured company and client data.

Five Remote Working Pro Tips That Will Set You Up for Success
Working remotely comes with many benefits and new challenges. Here’s what to consider when choosing to work remotely.

