With nearly 7 billion smartphones used worldwide, we’ve all come to rely on these handheld devices for everyday activities. We trust them to be the gateway for nearly every app and service, from banking to social media browsing. Unfortunately, this convenience and widespread adoption has also made smartphones a prime target for cybercriminals.
So, let’s review some practical advice on how to know if your phone is hacked and what you can do about it.
What is phone hacking?
Phone hacking refers to gaining unauthorized access to a smartphone and its data, whether through advanced techniques, intercepting unsecured connections, or even physically stealing the phone.
When someone hacks a phone, they can get access to your personal information—emails, contacts, banking credentials, and more. Cybercriminals can sell this sensitive information on the dark web, use it for identity theft, or commit other cybercrimes.
Want to make life harder for scammers?
How to know if your phone is hacked
Phone hacking typically happens when someone falls into a trap set by a hacker, such as clicking a phishing link or downloading apps from unauthorized sources. Hackers are clever and employ a variety of cyberattacks to deceive and illegally obtain access to your phone.

Here are some of the most common ways a cybercriminal can hack your phone:
- Malware: Malware can infect your device and steal information, damage files, or take control of your system without your permission. In phones, you may find the following types of malware:
—Keyloggers: These programs secretly record everything you type on your phone, including passwords, credit card details, and other sensitive information.
—Trojans: Like the famous Trojan horse, these malicious programs disguise themselves as harmless apps or files but actually contain harmful code that can give hackers control over your device. - Phishing: Hackers use fraudulent emails or messages to trick you into revealing personal information or clicking on malicious links that can compromise your phone's security. All the hacker needs to do is craft a convincing email or text message, circulate it, and wait for someone to take the bait.
- Control messages: Sometimes, hackers send specially crafted text messages or commands to exploit your phone's software vulnerabilities. These messages can contain malicious code that, when opened, gives the attacker control over your device. This is why jailbreaking isn’t recommended. Overriding the manufacturer’s security restrictions might expose your phone’s operating system to vulnerabilities.
- SIM swapping: In 2019, Twitter’s then-CEO Jack Dorsey fell prey to a group of SIM swappers. These hackers bypass security measures by tricking your mobile service provider into transferring your phone number to a new SIM card, thereby gaining access to your phone. Once the new SIM is activated and the old one discarded, they use it to impersonate the owner.
- WiFi and Bluetooth: Hackers can intercept unsecured WiFi and Bluetooth connections in range of your device. They can manipulate the data transmitted to and from your phone, potentially compromising your security and privacy. Other wireless communication technologies like near-field communication (NFC), primarily used for contactless payments, also have security risks that hackers can exploit to access your financial data, modify your transaction details, and more.
- Cables: It’s rare, but malicious USB cables or charging ports can be used to sneak harmful code onto your phone when you connect. Corrupted phone cables and public charging stations can give hackers access to your device without permission.
- Cryptominers: Cryptominers secretly install mining software on your phone and use its processing power to generate cryptocurrency. This kind of hacking, known as cryptojacking, drains your phone without your knowledge and overheats it, leading to poor performance and battery life. It's not just about the annoyance, though—cryptomining can also put your device's security at risk by opening a backdoor for hackers to steal your data.
- Stingrays: Fake cell towers, also known as IMSI catchers or “Stingrays” were originally built as a surveillance technique for law enforcement agencies; now, hackers use them to intercept and monitor mobile communications. These devices mimic legitimate cell towers, tricking your phone into connecting to them. Once connected, hackers can eavesdrop on your calls, intercept text messages, and even track your location.
- Spyware: Spyware allows hackers to monitor your activities, access your personal information, and potentially record your conversations. An example is Pegasus, one of the most sophisticated and potent spyware programs, which has been allegedly used to track political leaders, journalists, and activists worldwide.
Who hacks phones?
Hackers target smartphone owners to steal personal information, demand ransom, and leak sensitive information, among other illicit activities. Most phone hackers fall into one of five groups:
- Cybercriminals: These individuals or groups engage in illegal activities online, including hacking phones, with the intention of financial gain. They often steal personal information, sell it on the dark web, and conduct fraudulent activities.
- Hackers and hacktivists: Hackers and hacktivists hack phones for various reasons, including political, business, personal, or ideological motivations, aiming to expose vulnerabilities, promote a cause, or disrupt systems.
- Scammers: These people use deceptive techniques to trick phone users into revealing personal information, often with the intention of financial fraud or identity theft. Scammers often orchestrate email phishing, so you should be skeptical of suspicious emails, texts, and phone calls.
- Insider threats: Insider threats come from within an organization. These individuals usually have authorized access to phones and exploit their privileges to gain unauthorized access or leak sensitive information.
- Government agencies: Some government intelligence agencies can hack smartphones as part of their national security and counterterrorism efforts. Under certain circumstances, they can exploit vulnerabilities in phone operating systems or use advanced spyware to gain access. By monitoring communications and tracking movements, they can gather crucial intelligence to uncover potential threats and protect citizens.
Ready to stand up against hackers? We’ve got you covered. Protect your devices and online data with these 8 hacker protection tips.
Signs your phone has been hacked
After seeing suspicious activity on your smartphone, the first question that will probably pop into your mind is: how can I tell if my phone has been hacked? Some telltale signs of phone hacking can help you identify if you've become a target.
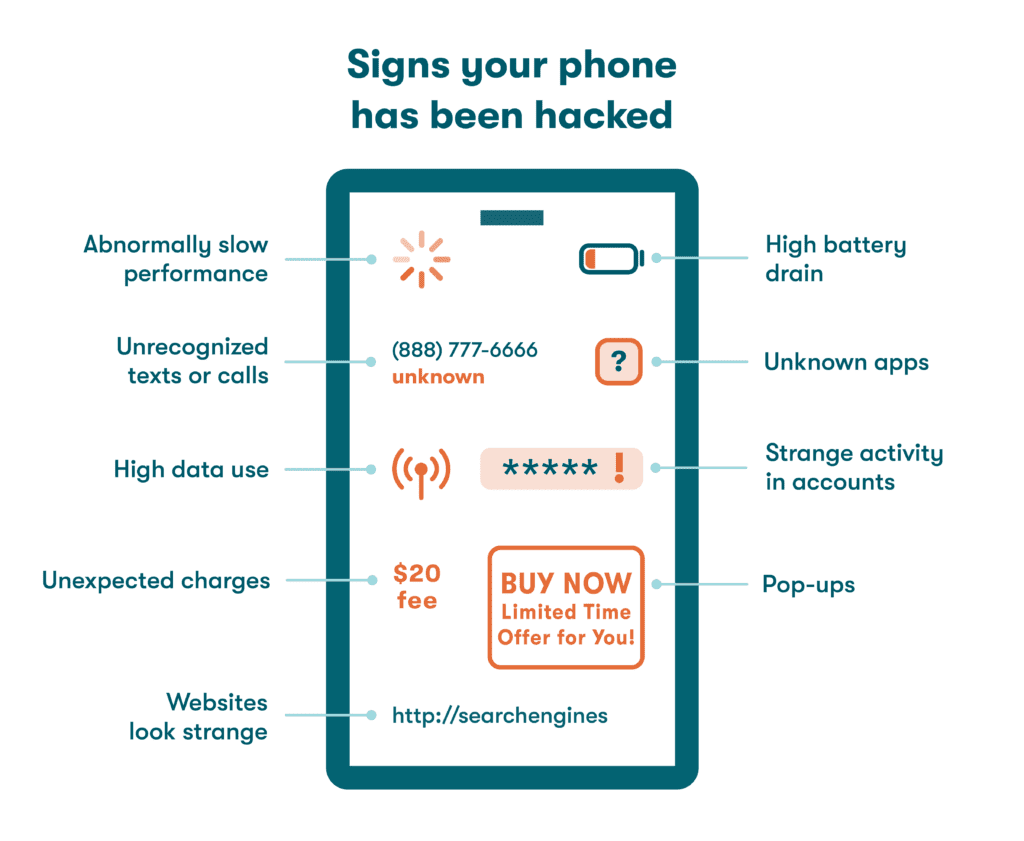
Look out for these signs to know if your phone is hacked:
- Unknown apps: If you see any unfamiliar apps on your phone that you don’t remember installing, this could mean a possible compromise. However, don’t confuse these apps with bloatware, which are the unnecessary pre-installed apps that come with your phone.
- High battery drain: If your phone battery drains too quickly, even with normal usage, it might be because of malicious processes running in the background.
- Abnormally slow performance: If your phone is suddenly sluggish and takes longer to open apps or respond to commands, it could be a sign of malware or unauthorized activity. If you experience dropped calls, missing texts, frequent freezes, crashes, or unexpected reboots, it might be due to unwanted background apps draining your phone's processing power.
- Strange activity on online accounts: If you notice suspicious activity, such as login attempts or changes to your account settings, it could mean that someone has gained unauthorized access to your accounts through your phone.
- Unrecognized texts or calls in your logs: Text messages or call records from unknown numbers in your phone might mean that someone else is using your phone or intercepting your communications. Consistently check your call logs for unusual activity and consider blocking and reporting unfamiliar numbers.
- Pop-ups: Are you seeing persistent and intrusive pop-up ads on your phone? These pop-ups, especially ones that appear outside of the apps you're using, can be a sign of adware infection. Avoid clicking or opening these pop-ups to prevent further issues.
- High data usage: Excessive data usage beyond your normal patterns, especially when you haven't changed your internet usage habits, could mean that malware or unauthorized processes are consuming data in the background.
- Websites look strange: If the websites you regularly visit suddenly appear distorted, have unusual layouts, or display unexpected content, it could mean your smartphone is compromised and you’re being redirected to unsafe websites.
- Unexpected charges on your phone bill: Unauthorized charges could result from unwanted apps that are consuming excessive data and causing additional charges. Some apps, known as fleeceware, can inflate your bill with unnecessary fees.
Can my phone camera be hacked?
If your phone has been compromised, it's possible for someone to remotely hack into your camera and spy on you in real time, especially when connected to unsecured public WiFi.
If you suspect unauthorized access to your camera, watch out for unfamiliar photos and videos in your gallery and be wary of the flash or recording icon unexpectedly activating. These signs may indicate that someone else has gained control over your camera without your knowledge.
What to do if your phone is hacked
If your phone’s hacked, you should act quickly to limit the damage. Here’s what to do if you think your phone has been hacked:
- Delete unrecognized or suspicious apps: Look closely at all your apps and uninstall anything that seems unfamiliar or suspicious. Sometimes hackers disguise malware as harmless background apps, so verifying and deleting any apps that raise concerns is important.
- Run anti-malware software: Use a reliable malware scanner and removal tool to thoroughly scan your phone for malicious software. This ensures that all traces of the hack are identified and removed.
- Turn off your personal hotspot and Bluetooth: Broadcasting your personal hotspot or keeping your Bluetooth on can expose your phone to potential hackers. Turn off your smartphone’s hotspot and Bluetooth when you aren’t using them, and set a strong password to prevent unauthorized access to your network.
- Change your passwords: Render your old passwords useless by updating all of them immediately. This restricts unauthorized access to your accounts and protects your personal information.
- Tell your contacts to ignore suspicious messages from you: Hackers may use your compromised device to send fraudulent or malicious messages, so alerting your contacts can help prevent them from falling for any scams or malware.
- Restore your device: Consider a factory reset as a last resort to eliminate malware from your phone. Remember that this step will erase all data stored on your device, so you should make a backup of your contacts, photos, notes, and other important files beforehand. Be cautious when resetting your phone to avoid unintentionally losing valuable data. You can restore Android and iPhone smartphones to their factory settings using their respective official guides.
How to protect your phone from being hacked
Small steps like keeping your phone updated and turning on security settings like 2FA will go a long way to safeguard your phone from hackers. Some of the best ways to keep your phone from getting hacked include the following:
- Keep your phone with you: One of the easiest ways to hack your phone is through physical access. Not leaving your phone unattended can greatly reduce the risk of it getting stolen and prevent unauthorized access to your device. Make sure to add a strong and unique passcode to your phone as an extra layer of security.
- Create strong passwords: Using weak passwords or reusing the same password for multiple accounts makes it easier for hackers to crack your passwords using brute force attacks. Instead, use unique and strong passwords for all your accounts to maximize security against these cyberattacks.
- Use a password manager: Password managers create strong, unique passwords for all your accounts. Advanced password managers, like Dashlane, often come equipped with additional security features, such as a VPN, 2FA, and dark web monitoring. You can even use them to securely store your banking credentials in a digital wallet, which strengthens the security and convenience of online shopping.
- Turn on 2-factor authentication (2FA): 2FA adds an extra layer of security by requiring more than just a password to access your accounts, making it harder for hackers to break in. You can also use biometric technology like facial recognition to enhance your security.
- Delete suspicious messages: Phishing is a common tactic to deliver malware or convince users to reveal private information. This is why you should be cautious of unexpected or suspicious calls, emails, and text messages, and avoid clicking on links or attachments from unknown sources.
- Clear your internet history frequently: Regularly clear your browser history, including cookies and cache, to prevent the profiling of your online activities and protect your privacy.
- Don’t use public WiFi without a VPN: Using unsecured public WiFi networks puts you at risk of being targeted by hackers. That’s why you should always use a virtual private network (VPN) to securely connect to an open WiFi network.
- Turn off your Bluetooth and hotspot when not in use: By disconnecting your phone from the internet and turning off Bluetooth, you create an "air gap" that prevents hackers from remotely accessing your device or installing malware.
- Avoid jailbreaking: Jailbreaking or rooting involves modifying your phone's operating system to bypass limitations set by developers or manufacturers. Although it allows you to make custom changes, it also weakens your phone's built-in security (as it runs on an unsupported operating system), making it easier for hackers to exploit vulnerabilities and install malware.
- Don’t download sketchy apps from unreputable sources: Check reviews and research before you install an app. If you're unsure or have doubts about its safety, it's best to avoid installing it altogether.
- Keep your phone and apps updated: Keep your apps and operating system updated by installing updates and patches when prompted. They often contain bug fixes and security enhancements that protect you from known risks and vulnerabilities.
- Use antivirus and anti-malware software: No matter how careful you are, hacks and malware can still find their way onto your phone. By regularly running reliable antivirus and anti-malware software, you can scan for and eliminate threats on your device while also receiving real-time protection that detects emerging threats.
- Lock your SIM card: Operating systems these days let you lock your phone and also your SIM card with a PIN to prevent unauthorized use. Doing so ensures your phone can only be used with your cellular network. If you have an Android smartphone, you can lock or unlock your SIM card by selecting More Security Settings in Security under Settings. Meanwhile, for an iPhone, you can access this by selecting SIM PIN in Cellular under Settings.
Protect your smartphone with Dashlane
With Dashlane, managing your passwords and more to protect your devices, accounts, and privacy is easy. Standard features like 2FA, a VPN, and secure password sharing lower the risk of hackers gaining access to your sensitive apps, contacts, and data on your smartphone.
Dashlane's encryption takes your device security to the next level. Using an AES 256-bit key for encryption, the digital wallet securely stores your payment information, making online transactions on your smartphone safer and more convenient. Plus, smart autofill helps you accurately enter login details without worrying about keyloggers or phishing.
Frequently asked questions (FAQs)
What’s the hardest phone to hack?
Android phones are targeted more by hackers because there are more of them out there, but iPhones are increasingly being targeted, too. iPhones are harder to hack because of their closed development environment, while Android devices are generally easier to hack because of the operating system's open nature.
Can my phone be hacked while turned off?
The short answer is no. Turning off your phone effectively stops most hacking attempts since there's no internet connection and no malicious code can be executed. However, it's worth noting that newer iPhone models enter a low-power state instead of fully powering off, which enables features like Find My iPhone. While it's unlikely, there's a small possibility that hackers could exploit this feature in the future.
Can someone hack your phone just by knowing your number?
Yes, but it's not easy for someone to hack your phone just by having your number. Most of the time, hackers use your number as part of a bigger plan. They might send you sneaky texts to trick you, track your whereabouts, send harmful links, or even intercept 2FA messages with spyware.
Can a website hack your phone?
Yes. Fake or malicious websites can hack your phone using techniques like drive-by downloads. Hackers can also exploit legitimate websites through malvertising pop-ups and banners, so it's important to stay vigilant and avoid interacting with suspicious online content.
References
- Statista, “Number of smartphones sold to end users worldwide from 2007 to 2021,” October 2022.
- McAfee, “McAfee 2023 Consumer Mobile Threat Report,” February 2023.
- Dashlane, “The Dark Web Iceberg Explained In Simple Terms,” June 2023.
- Dashlane, “11 Cyber Threats To Be Aware of & Defend Against,” April 2023.
- Kaspersky, “What is a Trojan horse and what damage can it do?”
- Kaspersky, “What is Jailbreaking – Definition and Explanation.”
- CNBC, “Here’s how the recent Twitter attacks probably happened and why they’re becoming more common,” September 2019.
- MakeUseOf, “5 Ways Hackers Use Public Wi-Fi to Steal Your Identity,” July 2022.
- MakeUseOf, “7 Security Risks You Need to Be Aware of When Using NFC,” June 2023.
- Forbes “How ‘Juice Jackers’ Plant Malware On Your Phone At Airports And Hotels,” April 2023.
- Wikipedia, “Cryptojacking.”
- Wikipedia, “IMSI-catcher.”
- Wikipedia, “Pegasus (spyware).”
- Dashlane, “Why Dashlane Will Never Ask You for Credentials in an Email (Because That’s How Phishing Works),” November 2021.
- Dashlane, “8 Hacker Protection Tips To Keep Your Online Accounts Safe,” May 2023.
- TechTarget, “What is bloatware? How to identify and remove it.”
- SafetyDetectives, “What Is Fleeceware & How to Prevent Fleeceware Scams in 2023,” June 2023.
- Dashlane, “5 Reasons Why You Should Back Up Your Computer Often,” May 2023.
- Samsung, “How to perform Factory Reset on Android smartphone?” October 2020.
- Apple, “How to factory reset your iPhone, iPad, or iPod touch,” June 2023.
- Dashlane, “What the Hack Is a Brute Force Attack?” February 2020.
- Dashlane, “Why You Need to Have Secure Passwords in 2023,” February 2023.
- Dashlane, “How a Password Manager Protects You and Your Data,” October 2022.
- Dashlane, "Are Digital Wallets Safe?" June 2023.
- Dashlane, “2-Factor Authentication 101: What It Is and Why It Matters,” June 2022.
- Dashlane, “Why Do You Need a VPN? Don’t Miss These 3 Key Benefits,” December 2022.
- Dashlane, “Why You Should Keep Your Apps Updated,” March 2022.
- Dashlane, "The Most Accurate Way to Autofill Forms on the Web."
- Dashlane, “Security and Privacy When You're Off the Clock.”
- Nord VPN, “Android vs. iOS: Security comparison 2023,” January 2023.
- Euronews, “Your iPhone can be hacked with malware even when it’s switched off, new research finds,” May 2022.
- McAfee, “How Do Hackers Hack Phones and How Can I Prevent It?” September 2022.
- Kaspersky, “How to remove a hacker from your smartphone.”
- Avast, “How to Know If Your Phone Has Been Hacked,” January 2023.
- Certo, “Can Someone Hack My Phone From My Number?” March 2023.
- NordVPN, “What is bluejacking? How to avoid bluejacking attacks,” January 2022.
- Dashlane, “Dark Web Monitoring.”
- CSO, “11 types of hackers and how they will harm you,” September 2020.
Sign up to receive news and updates about Dashlane