The internet connects us to information, commerce, and entertainment from all over the world. The Internet of Things (IoT) joins the digital and physical world by connecting ordinary objects and people to the cloud—and to each other.
Like all breakthroughs in technology, this new level of connectivity brings risks and cybersecurity threats that make Internet of Things security essential.
What is IoT security?
The idea of an Internet of Things streaming information from everyday objects originated almost 40 years ago when university students experimented with sensors installed in soda vending machines to track their contents remotely. In recent years, improved sensor technology, lightning-fast 5G wireless communication, and edge computing data centers close to users have made IoT use cases like smart speakers, connected security systems, and wearable health monitoring devices a reality.
IoT security is defined as the collection of cybersecurity tools and practices used to protect these IoT devices and their respective networks and users from cyberattacks and data breaches.
Why is IoT security important?
With the number of IoT devices expected to reach almost 30 billion by 2030, the potential for tampering and unauthorized use continues to grow. Many IoT devices do not include built-in security features, which creates a large number of unprotected endpoints for cybercriminals to target. In addition, many IoT devices operate over unencrypted channels and are not monitored by network security systems.
IoT security practices (and their benefits)
The variability and limited built-in security features of IoT devices make it difficult, but not impossible, to implement effective IoT security practices. When applied correctly, available IoT cybersecurity tools and tactics enable you to:
- Use encryption. Information transmitted to and from IoT devices might include confidential information that must be safeguarded. Ciphering messages through encryption makes them unreadable and unusable to cybercriminals, which lessens the impact of a data breach and helps protect the integrity and privacy of both users and their interconnected devices.
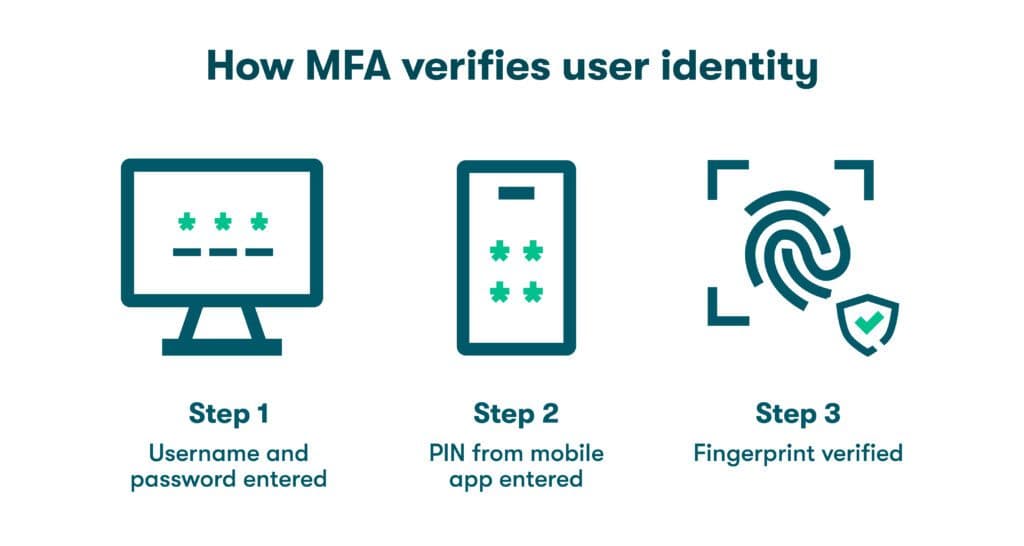
- Use multi-factor authentication. Multi-factor authentication (MFA) uses 2 or more identifiers, sometimes including biometric factors like fingerprints or facial recognition to reduce the risk of unauthorized IoT device access.
- Keep software updated. Each new software release for an IoT system or device is likely to include security updates and bug fixes along with performance improvements. Keeping software updated or establishing automatic updates prevents cybercriminals from taking advantage of published open-source vulnerability lists associated with previous IoT software revisions.
- Monitor IoT devices. Although IoT device monitoring is beyond the scope of many conventional network monitoring tools, new IoT monitoring and management platforms are being developed to meet the growing demand for IoT cybersecurity. The capabilities and benefits of these tools vary depending on the intended application, but most are designed to detect unusual activity while providing real-time insight into IoT performance and device availability.
- Use network segmentation. The practice of network segmentation builds secure walls around critical network assets by partitioning a computer network into multiple segments or sub-networks that function independently. Segmentation allows administrators to control which users and other devices can communicate with specific IoT devices while limiting the attack surface if there is a security breach.
- Protect credentials. More sophisticated IoT devices like self-driving cars, home security systems, and medical devices are typically password-protected to prevent unauthorized use. IoT credentials should be protected by updating the default credentials of the device, limiting password sharing to secure channels, and avoiding credential reuse that allows multiple accounts to be impacted if passwords are lost or stolen.
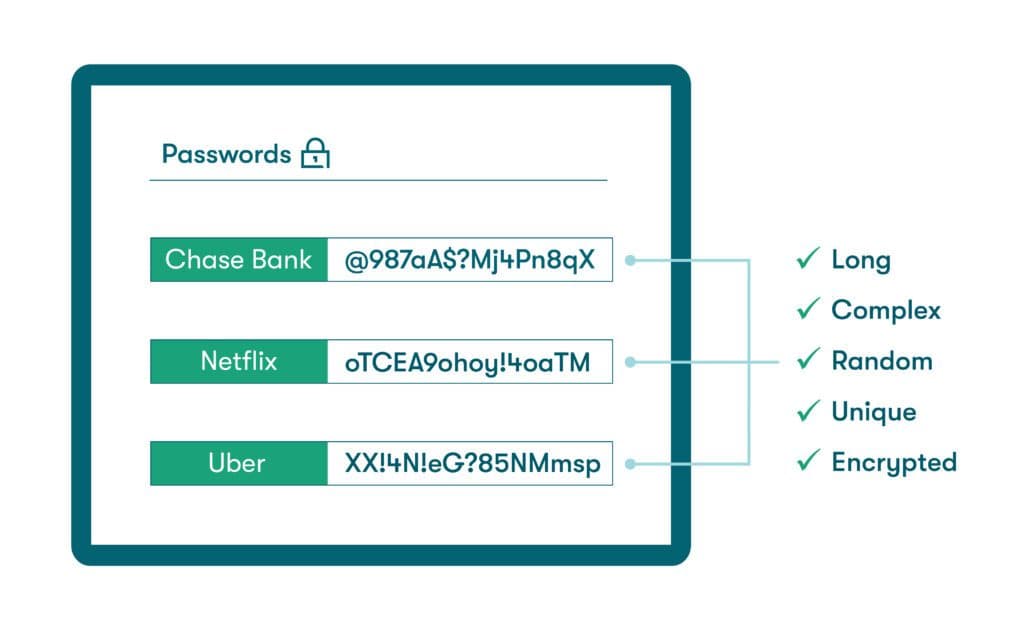
Strong passwords include a random mixture of at least 12 uppercase letters, lowercase letters, numbers, and special characters. This makes them much less likely to be guessed or otherwise cracked by cybercriminals. The best way to create strong, unpredictable credentials consistently is by using the password generator feature of a password manager.
Common challenges of IoT security
The need for basic cybersecurity for Internet of Things devices is underscored by the growing list of IoT security challenges. While many of these drawbacks are gradually being addressed through new security systems and technology, they should always be considered by designers, manufacturers, and users when new IoT applications are developed and deployed.
- Weak authentication: 2FA and MFA are highly effective additional layers of authentication, but many IoT devices lack this basic level of protection due to their limited computing power. Some IT administrators choose to secure IoT devices by using digital certificates to authenticate device identity while establishing secure connections by encrypting data transmissions.
- Software vulnerabilities: Timely software updates and patching are fundamental IoT device security concepts due to the inherently high number of IoT software vulnerabilities. The restricted settings and limited processing power of many IoT devices make it easier to exploit software vulnerabilities related to unsecure data transmission, lack of device management, and outdated electronic components.
- Physical security risks: By their nature, IoT devices are often deployed in dispersed and unprotected remote environments. This can leave them subject to undetected tampering, vandalism, and harsh weather. Physical security risks can be mitigated by implementing precautions like secure enclosure designs, surveillance systems, and tamper-evident seals.
- Data privacy concerns: Cybercriminals have little interest in collecting routine IoT sensor data on temperature settings, location, and usage patterns. However, a data breach that uses an IoT device as a gateway can also expose personal information like names, addresses, social security numbers, and medical records. Data privacy concerns are introduced when inadequate cybersecurity tools and processes protecting IoT devices leave personal information vulnerable. And the companies involved can suffer serious brand reputation and legal consequences.
- IoT device proliferation: The number of IoT devices is expected to double by 2030, highlighting the importance of the Internet of Things to society just as it magnifies security concerns and challenges. More IoT devices create a larger, more diverse attack surface that will make it progressively harder to detect and ward off physical threats, software vulnerabilities, and intrusions.
How to identify your IoT security needs
Your IoT security requirements will vary significantly depending on the type, number, function, and location of IoT devices deployed. Before you implement new security tools or systems, it is important to assess your unique IoT security needs:
- Take stock of all IoT devices. You need to know precisely which IoT devices are present on the network before you can assess your security needs since each device has unique data flow and data protection characteristics. Many simpler IoT devices can connect to the network autonomously, which precludes them from being included in endpoint security scans.
- Conduct a risk assessment. A cybersecurity risk assessment is a systematic process used to identify things like misconfigurations, outdated firmware, and vulnerabilities that exist on the overall network as well as individual IoT devices. A thorough risk assessment also includes a deeper dive into the tactics, techniques, and procedures (TTPs) used by cybercriminals who exploit IoT vulnerabilities, as well as their likelihood of occurrence.
- Perform cybersecurity audits. Once you know exactly what devices and vulnerabilities are in scope, cybersecurity audits allow you to compare current security risks and threats to your current security tools and protection strategies to determine whether they are adequate. The weaknesses and regulatory gaps you identify during the auditing process can be addressed proactively to prevent larger security or compliance problems from occurring later.
- Utilize penetration testing. You can secure IoT devices by hiring security experts to seek out potential data breach pathways in a controlled fashion. Penetration testing is used to assess IoT security by simulating real-world cyberattacks and reviewing the detection and response capabilities of existing security measures.
4 steps to implementing an IoT security policy
Once you have reviewed your security landscape carefully, you can either roll relevant IoT device security concepts into your existing cybersecurity policy or create a standalone policy dedicated to IoT issues and challenges. Important steps to consider as you finalize this policy include:
- Creating an access management plan: Access management is one of the biggest challenges IoT administrators face, since each device type has different resource constraints and security requirements. An all-encompassing IoT access management plan helps to prevent unauthorized access and data breaches by defining the appropriate access policies and user authentication mechanisms.
- Creating an incident response plan: The IoT ecosystem places billions of devices into environments where physical damage, malware infections, and compromised data transmissions are difficult to eliminate. A detailed incident response plan allows you to react to security incidents and contain the damage faster. Incident response plans also define roles and responsibilities to make collaboration with external parties like IoT device manufacturers more efficient.
- Using a password manager: A password manager helps to protect IoT devices and their users from cybercriminals who steal or guess credentials to gain unauthorized network access. The best password managers raise your security profile by creating strong credentials for each account and storing them in a secure, encrypted vault. Automatic password generation features and customizable autofill improve both security and convenience while eliminating the need to create and remember strong credentials for each device or account.
- Training and educating employees: As IoT technology continues to transform physical objects into data-streaming extensions of the digital world, human nature assures us that many users will approach these devices casually and neglect important security elements. Continuing to train and educate employees and other users on IoT device security concepts is a good way to keep these issues visible as part of the overall security culture.
How Dashlane helps protect IoT
IoT security will continue to grow in importance as the technology and applications spread. Dashlane proactively supports this evolution by minimizing weak and reused passwords and encrypting data to prevent unauthorized access.
Additional features like VPN, 2-factor authentication, a secure sharing portal, and Dark Web Monitoring round out the comprehensive cybersecurity solution, while a patented zero-knowledge architecture ensures that no one, including Dashlane, can access your private information.
Dashlane’s industry-leading innovations around credential management empower individuals and organizations to explore IoT with confidence.
References
- Vision of Humanity, “IoT Technologies Explained: History, Examples, Risks & Future.”
- Exploding Topics, “Number of IoT Devices (2024),” February 2024.
- Dashlane, “Is My Smart Fridge Listening to Me? And Other Concerns,” April 2022.
- Dashlane, “A Complete Guide to Asymmetric Encryption: Definition & Uses,” March 2023.
- Dashlane, “A Complete Guide to Multifactor Authentication,” November 2022.
- Dashlane, “Why You Should Keep Your Apps Updated,” March 2022.
- Logit, “The Top 10 Iot Monitoring Tools,” March 2024.
- Dashlane, “What is Network Segmentation & How Does It Work?” February 2024.
- Dashlane, “Could My Self-Driving Car Get Hacked?” April 2022.
- Venafi, “Top 10 Vulnerabilities that Make IoT Devices Insecure,” July 2023.
- Dashlane, “What Is Data Privacy & Why Is It Important?” April 2023.
- Dashlane, “4 Most Common Types of Inherent Risks for IT & Cybersecurity,” February 2024.
- Dashlane, “How to Conduct Your Own Internal Security Audit,” April 2021.
- Cloudflare, “What is penetration testing? | What is pen testing?”
- NCBI, “Access Control for IoT: A Survey of Existing Research, Dynamic Policies and Future Directions,” February 2023.
- Dashlane, “How to Prevent Ransomware Attacks on Your Devices,” March 2023.
- Embedded, “Automating the IoT incident response process,” December 2019.
- Dashlane, “Build the Case for a Password Manager in 8 Steps.”
- Dashlane, “The Importance of Building a Strong Security Culture.”
- Dashlane, “Dashlane's Security Principles & Architecture.”
- Dashlane, “A Brief History of Passwords,” 2021.
Sign up to receive news and updates about Dashlane
Related articles