business security

Closing the Credential Risk Visibility Gap: What Our VP of Product Shared with 100+ Security Execs
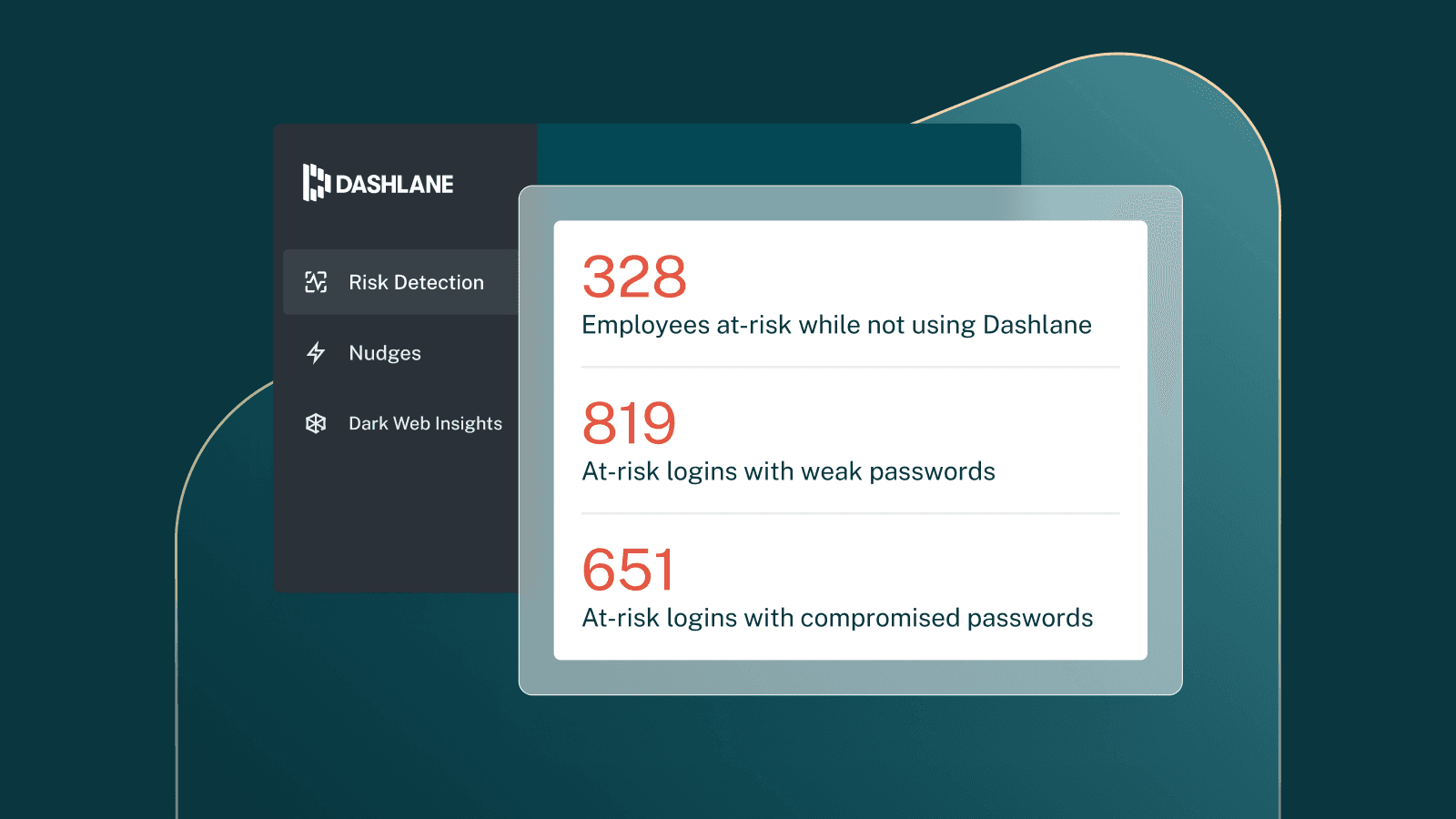
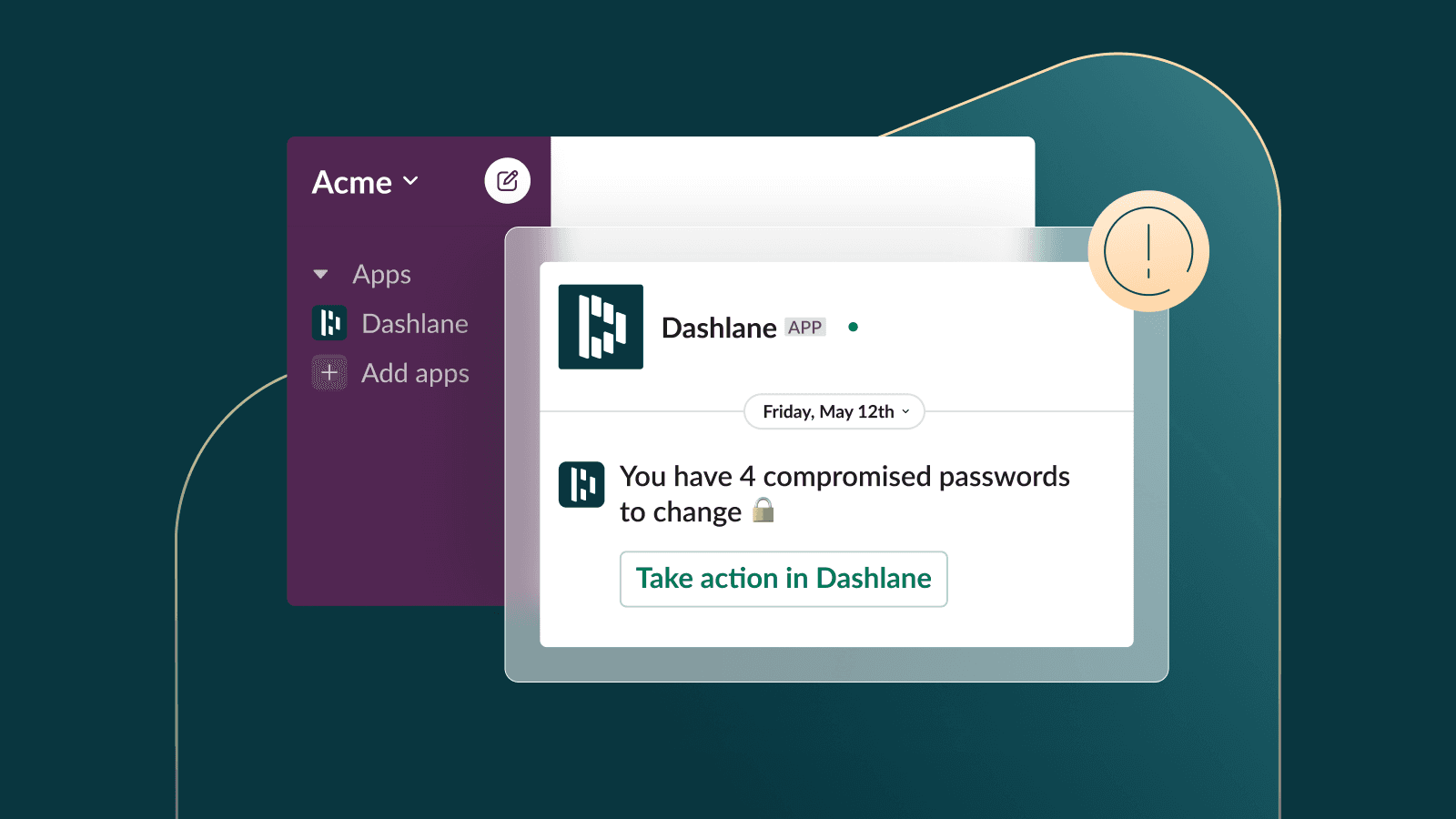
Credential risk visibility is a major business need. Dashlane’s VP of Product shares how Credential Risk Detection can help.
New Data Shows Traditional Approaches to Credential Security Fail the Modern Workforce
As part of our credential security report series, learn why traditional approaches to business credential security simply aren’t working.

How to Build the Case for a Credential Manager: Answers to Common Concerns
To help your organization’s decision makers understand the value of a credential manager, review these 5 common concerns and how to respond.

How to Build the Case for a Credential Manager: The Cost of Doing Nothing
Not having a standalone credential manager comes with high costs to your organization’s security, productivity, and reputation.

New Data Shows Impact of AI-Powered Phishing on Businesses
As part of our credential security report series, discover new data about how AI is accelerating phishing attacks against businesses.

Unlock Seamless Access with the Dashlane Public API
The new Dashlane Public API gives organizations secure access to key data that helps them streamline operations and enhance security.

How Privacy Computing Protects Personal & Professional Data
Learn about privacy computing and how it protects personal and professional data with encryption, zero-trust, and secure data practices.

8 IoT Risks Every Organization Needs to Be Aware Of
Discover 8 key IoT risks, from data breaches to malware, and learn how to protect your business with strong IoT security strategies.
Q&A with Dashlane’s CTO: How Security Leaders Can Address Major Causes of Breaches
Dashlane CTO Frederic Rivain shares his thoughts on how security leaders can achieve more proactive security, what gives him hope, and other insights.

How SSH Keys Can Transform Your Organization’s Security
Securing SSH keys is crucial for your organization’s security. Learn best practices to prevent unauthorized access, ensure data integrity, and protect your network.